Blogs about AppSec

Legit Security Named 2026 AI Code Innovator in AppSec, Leader in AppSec Management
Legit Security recognized as a leader in AppSec for innovating AI code security. Discover the award-winning VibeGuard platform.
Read More.png?width=740&height=220&name=image%20(42).png)
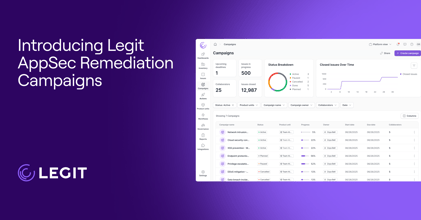
Legit License Scanning and Policy Enforcement
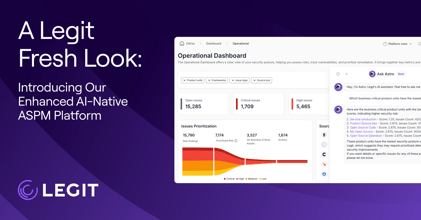
Upgraded Custom ASPM Dashboards: Build Security Views That Match How Your Teams Work
Read More.png?width=740&height=220&name=image%20(44).png)
Software License Scanning vs. Manual License Review: The True Cost of Compliance
Upgraded Custom ASPM Dashboards: Build Security Views That Match How Your Teams Work
Read More
Upgraded Custom ASPM Dashboards: Build Security Views That Match How Your Teams Work
Upgraded Custom ASPM Dashboards: Build Security Views That Match How Your Teams Work
Read More
Executive Brief: Questions AI is Creating that Security Can't Answer Today
Executive Brief: Questions AI is Creating that Security Can't Answer Today
Read More
Technical Architecture Guide: Fixing Code Issues Early to Protect Developer Flow
Technical Architecture Guide: Fixing Code Issues Early to Protect Developer Flow
Read More
The AI Security Maturity Model for AI-First Development Teams
The AI Security Maturity Model for AI-First Development Teams
Read More
When Security Incidents Break: The Questions Every CISO Asks (And How We Securely Built a Solution in Record Time)
When Security Incidents Break: The Questions Every CISO Asks (And How We Securely Built a Solution in Record Time)
Read More
Enterprise POV: Why AI Policy Without Enforcement Fails at Scale
Enterprise POV: Why AI Policy Without Enforcement Fails at Scale.
Read More
What Breaks First When AI-Generated Code Goes Ungoverned?
What Breaks First When AI-Generated Code Goes Ungoverned?
Read More



.jpg?width=740&height=220&name=Blog-Image-Reality%20Check%20on%20Securing%20AI-Generated%20Code-2%20(1).jpg)
-1.png?width=740&height=220&name=2%20(2)-1.png)









The 2025 State of Application Risk Report: Understanding AI Risk in Software Development
Get details on the AI risks Legit unearthed in enterprises' software factories.
Read More
Strengthening Software Security Under the EU Cyber Resilience Act: A High-Level Guide for Security Leaders and CISOs
Get guidance on key tenets of the EU CRA and how Legit can help address them.
Read More.png?width=740&height=220&name=Legit-NewAICapabilities-2%20(1).png)

How Legit Is Using Classic Economic Tools to Prevent Application Vulnerabilities
Prevent vulnerabilities and learn how Legit uses data-driven methods like the Lorenz Curve and the Gini Index to uncover high-risk areas in your SDLC.
Read More.png?width=740&height=220&name=ASPM_1200x627%20(2).png)


The Power of Identifying Continuously Vulnerable Repositories (CVRs)
Legit Security is redefining application security by analyzing CVRs, helping enterprises prevent vulnerabilities from recurring in their SDLC.
Read More



Legit SLA Management & Governance – Built for Enterprise-Scale AppSec
Get details on Legit's powerful SLA management capabilities.
Read More
The 2025 State of Application Risk Report: Understanding Toxic Combinations in Application Security
Get details on the most common toxic combinations Legit unearthed in enterprises' software factories.
Read More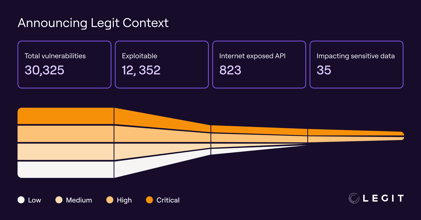

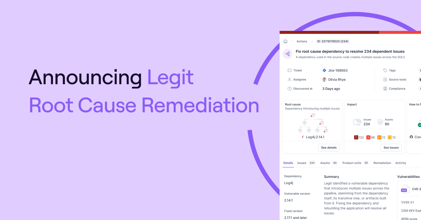

.png?width=740&height=220&name=Blog%20Thumbnail%20(1).png)
White House Executive Order: Strengthening and Promoting Innovation in the Nation’s Cybersecurity
Get details on this new cybersecurity Executive Order and its implications.
Read More
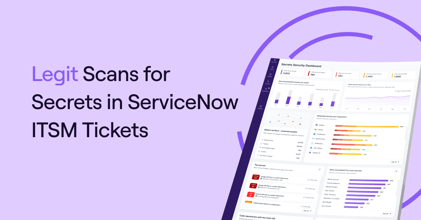


How to Reduce Risk From Exposed Secrets
Understand how secrets end up exposed, and how to prevent this risk.
Read More
Unlocking the Power and Potential of GenAI in Software Development
GenAI's rapid adoption brings with it significant challenges in security, governance, and visibility.
Read More
How to Reduce Risk From Developer Permissions Sprawl
How to Reduce Risk From Developer Permissions Sprawl. Get steps to prevent risky permissions sprawl in your SDLC.
Read More
How to Reduce Risk From Misconfigured Build Assets
How to Reduce Risk From Misconfigured Build Assets. Get steps to prevent risky misconfigurations in your SDLC.
Read More
Software Security Best Practices: Where to Focus First
Software Security Best Practices: Where to Focus First. Get our recommendations on where to focus your software security efforts.
Read More
How to Mitigate the Risk of GitHub Actions
How to Mitigate the Risk of GitHub Actions. Get highlights of our research into the security of GitHub Actions, and our advice on mitigating the risk.
Read More
The Risks Lurking in Publicly Exposed GenAI Development Services
The Risks Lurking in Publicly Exposed GenAI Development Services. Get our research team's analysis of the security of GenAI development services.
Read More
ESG Survey Report Finds AI, Secrets, and Misconfigurations Plague AppSec Teams
ESG Survey Report Finds AI, Secrets, and Misconfigurations Plague AppSec Teams. Find out how your peers are managing application security challenges.
Read More
Preview of State of GitHub Actions Security Report: Security of GH Workflows Building Blocks
Security of the Building Blocks of GitHub Actions Workflows. Understand the security status of GitHub Actions workflows and how to mitigate the risk.
Read More
Why Legit Security Immediately Joined the New Coalition for Secure Artificial Intelligence (CoSAI)
Why Legit Security Immediately Joined Google’s New Coalition for Secure Artificial Intelligence (CoSAI). Get details on CoSAI and why Legit chose to be a part of this forum.
Read More
Security of Custom GitHub Actions
Security of Custom GitHub Actions. Get details on Legit's research on the security of custom GitHub Actions.
Read More
Announcing The State of GitHub Actions Security Report
Announcing the State of GitHub Actions Security Report. Get details on Legit's research on the security of GitHub Actions.
Read More
EU Cyber Resilience Act: Updates and Important Requirements
Ensure compliance with the EU Cyber Resilience Act. Learn CRA essentials, how to secure digital products, and how Legit Security helps automate compliance and risk management.
Read More
What is ASPM? Application Security Posture Management 101
Learn how Legit Security enhances Application Security Posture Management (ASPM) by automating key processes to ensure business protection.
Read More.png?width=740&height=220&name=Blog%20-%201200%20x%20627%20(2).png)
Security Challenges Introduced by Modern Software Development
Security Challenges Introduced by Modern Software Development. Understand how modern software development is changing security threats.
Read More
Don’t Protect Your Software Supply Chain, Defend the Entire Software Factory
Don't Protect Your Software Supply Chain, Defend the Entire Software Factory. Find out why a too-narrow definition of "supply chain" may be hindering software security efforts.
Read More
Securing the Gateway: Why Protecting Build Systems Is Crucial in Modern Software Development
Securing the Gateway: Why Protecting Build Systems Is Crucial in Modern Software Development. Understand why securing build systems is as important as securing production systems.
Read More
New Survey Finds a Paradox of Confidence in Software Supply Chain Security
New Survey Finds a Paradox of Confidence in Software Supply Chain Security. Get results of and analysis on ESG's new survey on supply chain security.
Read More
Verizon 2024 DBIR: Key Takeaways
Verizon 2024 DBIR Key Takeaways. Get key data points and takeaways from the 2024 Verizon Data Breach Investigations Report.
Read More
Securing the Vault: ASPM's Role in Financial Software Protection
Discover the importance of Application Security Posture Management (ASPM) in financial software protection. Learn how ASPM enhances security practices and compliance in the U.S. financial services sector through Legit Security.
Read More.png?width=740&height=220&name=Blog%20-%201200%20x%20627%20-%20Ofek%20Haviv%20(V2.1).png)
Dependency Confusion Vulnerability Found in an Archived Apache Project
Dependency Confusion Vulnerability Found in an Archived Apache Project. Get details on the Legit research team's discovery of a dependency confusion vulnerability in an archived Apache project.
Read More
How to Reduce the Risk of Using External AI Models in Your SDLC
How to Reduce the Risk of Using External AI Models in Your SDLC. Understand how AI models add risk and how to address it.
Read More
Securing the Software Supply Chain: Risk Management Tips
Securing the Software Supply Chain: Risk Management Tips. Securing the software supply chain can seem daunting, but with the right strategy, you can optimize your software supply chain risk management practices.
Read More

How to Get the Most From Your Secrets Scanning
How to Get the Most From Your Secrets Scanning. Secret scanning is essential for unlocking next-level software supply chain security. Get tips & best practices for optimal secret scanning to secure your code.
Read More
Microsoft Under Attack by Russian Cyberattackers
Microsoft Under Attack by Russian Cyberattackers. Understand how these attackers are operating and what their tactics mean for security strategies.
Read More
Don't Miss These Emerging Trends in Cloud Application Security
Don't Miss These Emerging Trends in Cloud Application Security. Get details on trends and best practices in cloud application security.
Read More
Using AI to Reduce False Positives in Secrets Scanners
Using AI to Reduce False Positives in Secrets Scanners. Get an overview of how secrets scanners work, and how Legit is reducing secret-scanning false positives..
Read More

Navigating the Shift: Unveiling the changes in PCI DSS version 4
Gain insights in the latest changes in PCI DSS version 4 with this quick overview, highlighting the primary changes and how to best prepare for them.
Read More




It's Time to Automate Your Security Testing w/ DevSecOps Tools
Your security is only as good as your team, so why leave it to chance? Learn how automated DevSecOps tools can radically boost your AppSec.
Read More
Rethinking Shift Left: Overcoming Context Gaps to Reduce AppSec & Developer Friction
Discover how ASPM reduces friction and shifts security left for AppSec and developers with deep context. Optimize your security strategy effectively.
Read More
SBOM Management Best Practices
Learn SBOM best practices for application security. Explore its evolution, significance, and optimization strategies for enhanced protection.
Read More

6 Cloud Application Security Best Practices You Can't Miss
Discover cloud application security best practices: risks, benefits, and strategies for a secure cloud environment.
Read More
Top Vulnerability Management Best Practices and Tips
Master vulnerability management best practices with our guide. Secure your organization using effective strategies and modern techniques.
Read More

What Is Cloud Security Posture Management? CSPM Explained
Discover how cloud security posture management (CSPM) helps identify cloud misconfigurations, enforce compliance, and safeguard against security risks.
Read More
An In-Depth Guide to the Vulnerability Management Lifecycle
Learn to master the vulnerability management lifecycle. Safeguard against threats, implement best practices, and ensure compliance.
Read More
Emerging Risks with Embedded LLM in Applications
Learn how the use of Large Language Models (LLMs) like OpenAI's GPT and Google's Bard can create security risks in your applications.
Read More.png?width=740&height=220&name=SEO%20Blog%20%2328%208%20Tips%20to%20Maximize%20Application%20Security%20Testing%20(1).png)
Application Security Testing: Types and Best Practices
Enhance your application security testing and identify vulnerabilities faster. Learn best practices and improve your applications with Legit Security.
Read More.png?width=740&height=220&name=SEO%20Blog%20%2326%20Stepping%20Up%20Cybersecurity%20An%20In-depth%20Look%20at%20SCA%20and%20SAST%20(4).png)
SCA vs SAST: Cybersecurity Comparison Tools
Compare SCA vs SAST to enhance cybersecurity. Understand their methods, benefits, and how they protect against software supply chain threats.
Read More.png?width=740&height=220&name=SEO%20Blog%20%2325%20Best%20Vulnerability%20Management%20Tools%20Used%20by%20Enterprises%20(4).png)
How to Choose the Right Vulnerability Management Tools
Discover core functions, benefits, and tips for selecting the best vulnerability management solutions to boost your cybersecurity efforts.
Read More.png?width=740&height=220&name=Blog%20SEO%20Blog%20%2322%20Embracing%20the%20Future%20of%20Secure%20Software%20Development%20A%20Comprehensive%20Look%20at%20the%20SSDF%20(3).png)
Embracing the Future of Secure Software Development: A Comprehensive Look at the SSDF
Explore the benefits of the Secure Software Development Framework (SSDF) and how it differs from traditional SSDLC. Learn how adopting SSDF improves security.
Read More.png?width=740&height=220&name=thumbnail_image%20(1).png)
Supply Chain Attacks Overflow: PyPI Suspended New Registrations
After PyPI paused new registrations due to a surge in malicious packages, learn how Legit Security helps protect your SDLC from supply chain attacks.
Read MoreRequest a Demo
Request a demo including the option to analyze your own software supply chain.