Cloud environments and the applications running on them present an enormous attack surface that’s frequently exploited. Protecting runtime environments in the cloud is certainly a top concern for any CISO, but solutions that detect and mitigate vulnerabilities in the cloud also bring operational challenges, noise, and remediation obstacles that can hinder an effective and efficient security program. That’s why Legit Security, a market leader in ASPM (Application Security Posture Management), has teamed up with CrowdStrike and their cloud security offerings to solve these challenges.
The challenges of securing cloud applications
When scanning your cloud assets for vulnerabilities, there are many hard challenges to overcome:
- The sheer volume of vulnerabilities and findings makes it difficult for security teams to prioritize which issues are most critical to address
- Vulnerabilities introduced within the code or deployment pipeline are usually deployed over-and-over again—even if addressed at runtime
- Identifying the root cause of a cloud vulnerability and determining the individual responsible for its resolution is typically a time consuming and complex task
These challenges make cloud remediation in isolation less effective and holds back the pace of development innovation. The answer to overcoming these challenges is shifting security left to address vulnerabilities in the pre-production code, CI/CD pipeline and development environment. By using Legit’s code to cloud ASPM pipeline discovery and visibility capabilities, it’s possible to trace each cloud vulnerability back to the application’s pipeline and source code.
Trace runtime cloud vulnerabilities back to their source
Runtime application security issues can manifest in multiple ways, such as through the application code, Infrastructure as Code (IaC), or CI configuration files. Pinpointing the exact origin of a vulnerability within the source code with all relevant context provides clarity and allows teams to harness deep understanding of the development environment to prioritize based on organizational risk and accelerate the remediation process. There are a few ways that this can be done:
- Identify who is responsible for resolution: In large organizations, various teams or individuals are responsible for different segments of the codebase. By identifying where a vulnerability originates, we can assess who is responsible and best equipped to handle the issue.
- Provide detailed remediation steps and context: When the root cause of a vulnerability is established, it becomes considerably simpler to chart out a clear and effective remediation plan. By understanding the context in which the vulnerability arose it is possible to address not just the symptom but the underlying issue.
- Detect and correlate similar vulnerabilities: Vulnerabilities might not always be isolated incidents. Once a particular vulnerability is traced back to its source code origin, we can identify if similar issues exist elsewhere in the organization source code. This proactive approach helps in ensuring that the organization's systems are robust and consistently secure.
- Establish preventative measures: By understanding the origins of their vulnerabilities, teams can set up guardrails, such as automated code reviews, testing protocols, or CI pipeline checks, to ensure that similar vulnerabilities are identified and remediated before they become threats.
Legit and CrowdStrike: Integrating ASPM and CSPM to solve these challenges
By leveraging CrowdStrike's cloud expertise in tandem with Legit Security's deep understanding of the software development lifecycle (SDLC), you can trace an application vulnerability detected by CrowdStrike Falcon Cloud Security back to its point of origin with a comprehensive set of development context within the Legit Security ASPM solution.
For example, if Falcon's container scanning identifies a container vulnerability, it can be traced back to the originating source repository using the Legit platform. This not only reveals the repository owner but also determines if security measures are in place within that repository and pinpoints the necessary modifications to the build process to rectify the vulnerability from ever happening again. It’s also possible to create an automation rule in Legit that notifies the code owner via Slack or an equivalent ticketing system as soon as the vulnerability is detected by CrowdStrike scanners.
An additional use case for the Legit and CrowdStrike integration involves monitoring vulnerabilities from code to cloud. For instance, if the Legit Platform identifies a secret in the code, it can use context provided by CrowdStrike to trace it to its deployment location and initiate a remediation process. This process can be used to eliminate the secret from both running applications and the original source code.
Here are some Legit Security platform screenshots showing a container tracked from source to cloud:
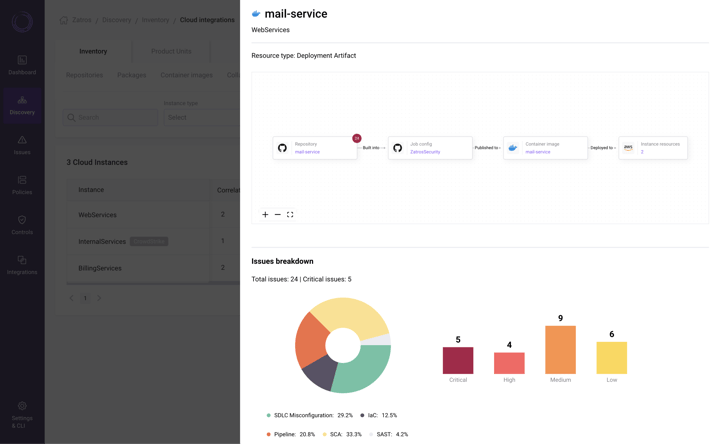
And here is a CrowdStrike container vulnerability shown within the Legit Security Platform:
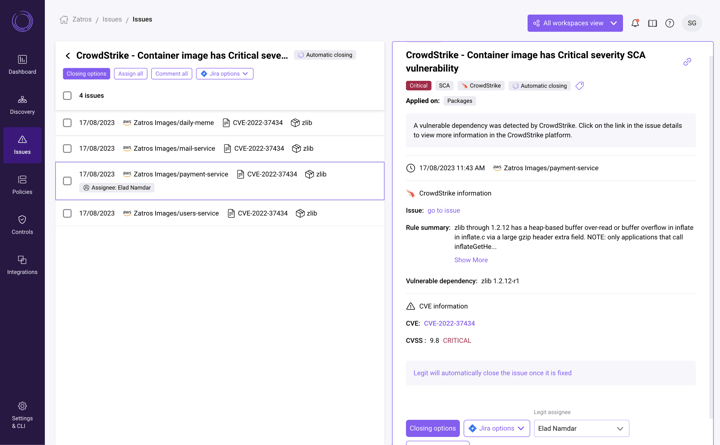
The collaboration between Legit and CrowdStrike offers customers an integrated solution encompassing both Application Security Posture Management (ASPM), which oversees every phase of the development pipeline, and CSPM, ensuring the cloud environments are optimally configured and safeguarded. Bridging our expertise, we enable organizations to seamlessly secure their environments from code to cloud. Collaborations like this are setting a new standard in cybersecurity, helping organizations safeguard every step of the SDLC, from development to deployment.
For more information about how Legit Security and Crowdstrike work together, download our Joint Solution Brief.
Ready to learn more? Schedule a product demo or check out the Legit Security Platform.
Download our new whitepaper.


