ASPM Platform You Can Trust
Legit is an AI-native ASPM platform that automates AppSec issue discovery, prioritization, and remediation. A trusted ASPM vendor for your AppSec and software supply chain security programs.
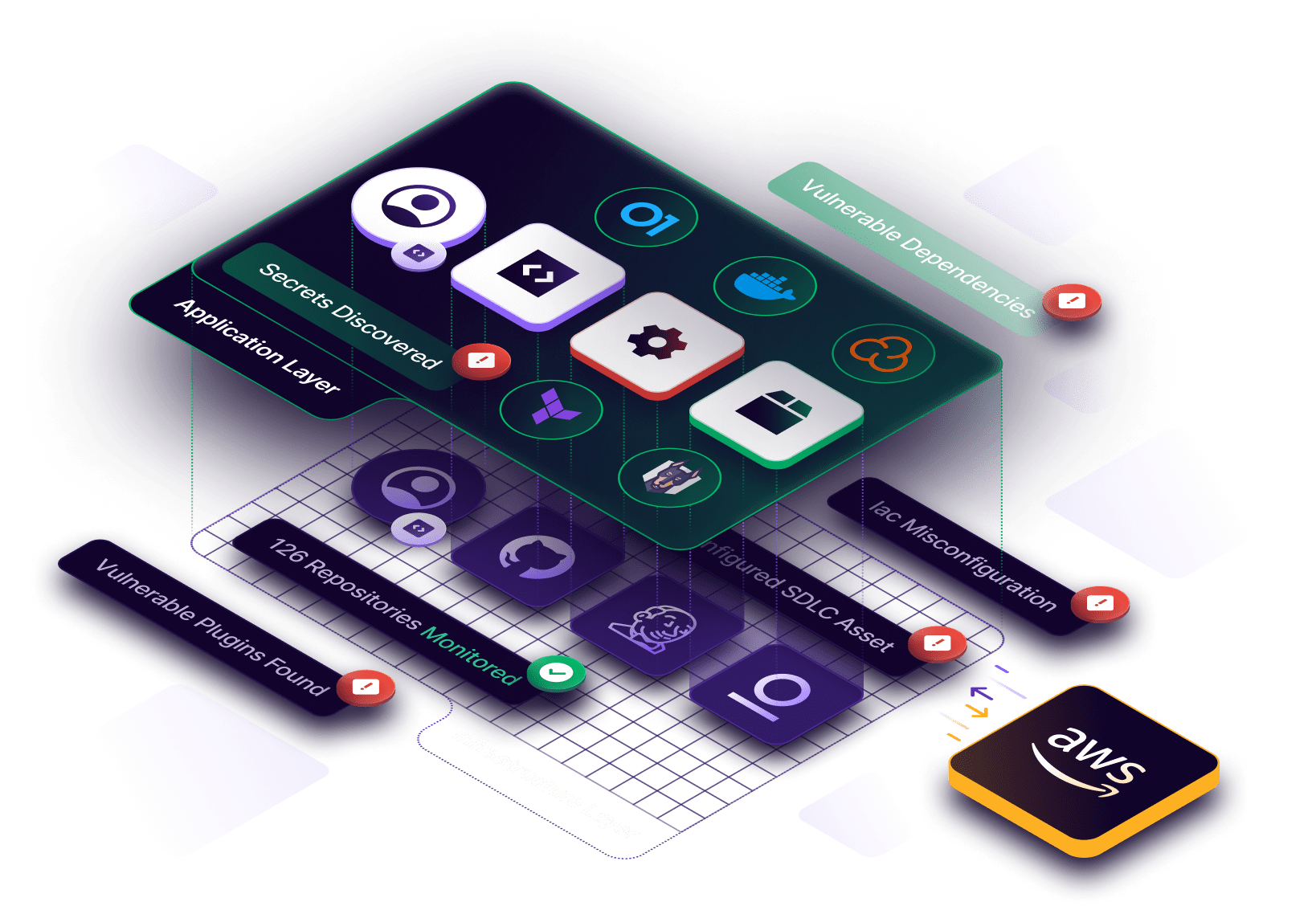
Why ASPM?
ASPM helps security teams manage risk, reduce development costs, and increase the speed of software delivery. ASPM provides a complete and real-time view of the software factory, its assets, its owners, its security controls, its vulnerabilities, and how they all relate. With this view, security teams can ensure AppSec controls are applied consistently – and early – in the software development lifecycle.

Mitigate AppSec Risk
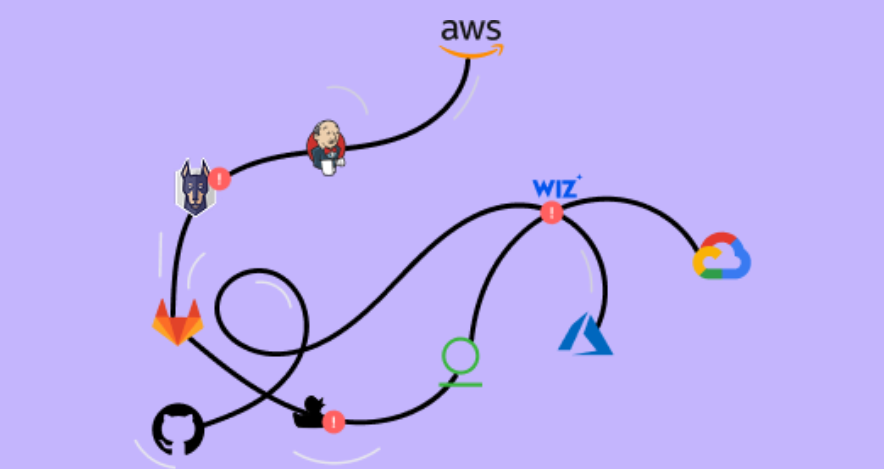
Code-to-Cloud Coverage
Integrate with the systems and AppSec test tools used to build and deploy applications for a central view of all vulnerabilities, misconfigurations, GenAI usage, secrets, and other areas of risk.
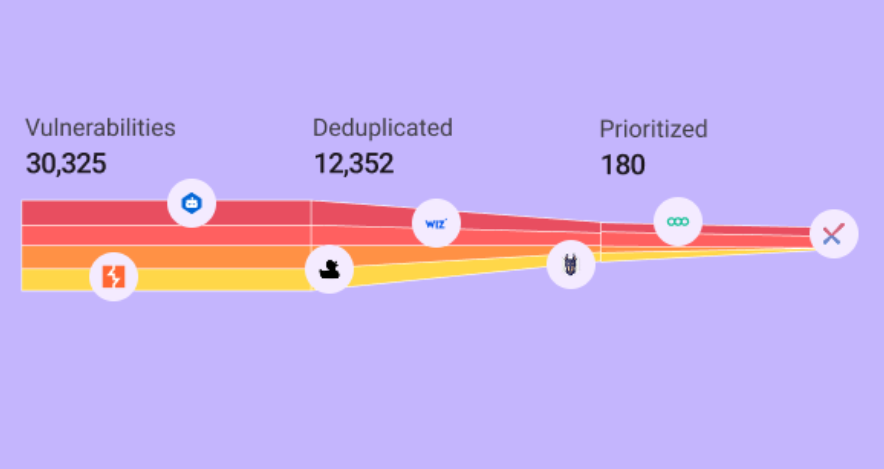
AppSec Orchestration, Correlation, & De-Duplication
Orchestrate AST scanning and correlate/de-duplicate data to identify exactly where actions can have the most material impact on risk reduction.
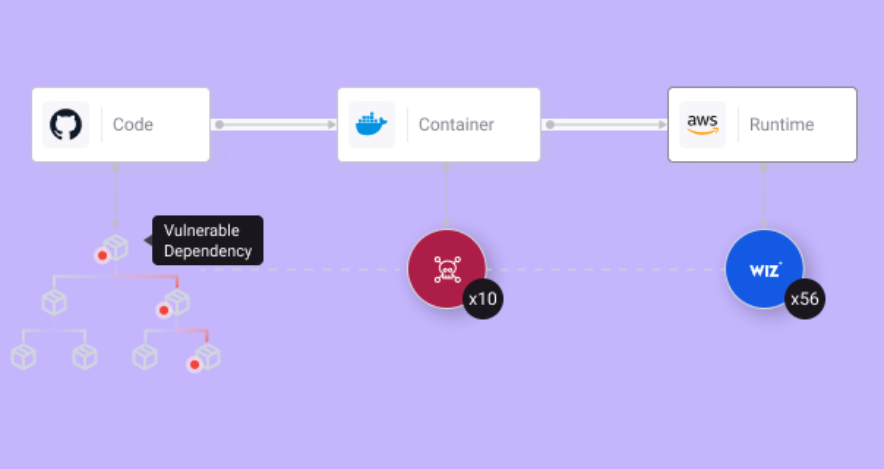
Root Cause Remediation
Identify chokepoints where remediation actions can address multiple issues at once to accelerate risk reduction and reduce the burden on developers.
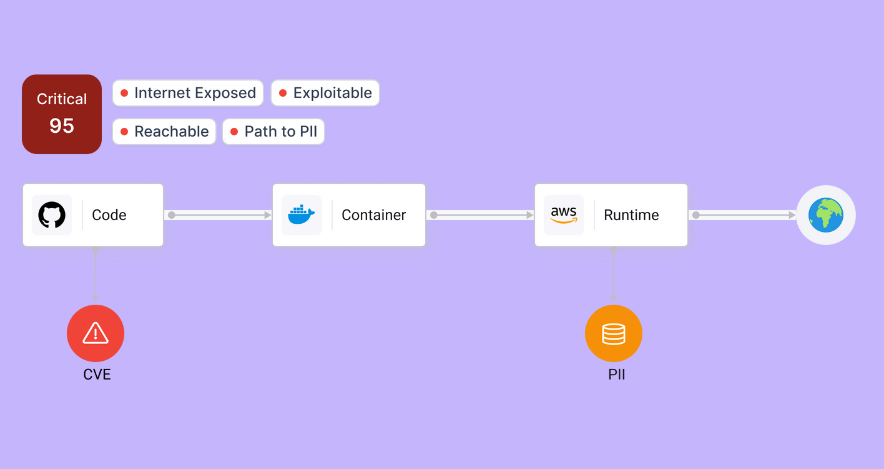
Contextualized Risk Scoring
Bring together disparate data points – including an application’s business criticality, compliance, GenAI use, APIs, and Internet accessibility – to determine fixes that really matter to the business.
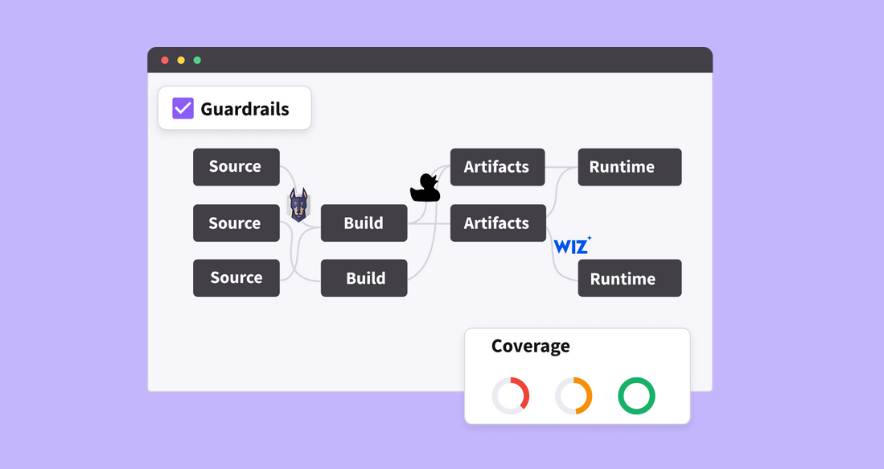
Risk Prevention
Get proactive by automating processes to enforce guardrails and policy. Legit positions teams to benefit from repeatability and elimination of significant manual effort.
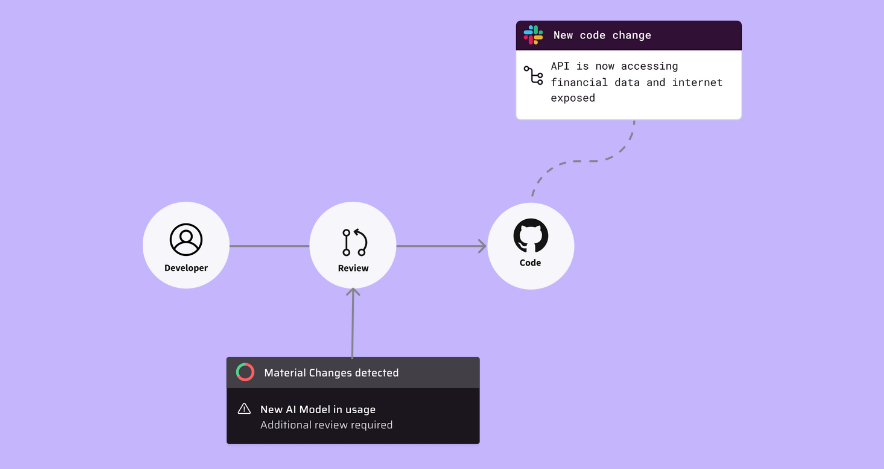
Material Change
Continually discover all elements of an application and the software development environment, to identify any changes that may elevate your AppSec risk.
Unify Security Across App & Product Teams
Sprawling application and product teams with unique tools, systems, and processes create visibility and policy challenges for CISOs and their teams. The Legit ASPM platform provides a consistent platform to manage policies and allows developers to work the way they wish without sacrificing security.
Enable AI-Powered Development – Securely
AI changed the game for application development and security. Over 90% of developers use AI coding tools, while more than 25% of new code is generated by AI. The Legit ASPM platform enables you to discover developers’ use of AI, identify AI-generated code, and enact guardrails to ensure GenAI is used safely and securely.
Shift Left to Reduce Costs, Increase Productivity
Despite best efforts, issues will always arise in the software development process. From misconfigurations in the dev environment to vulnerabilities in code to issues created by GenAI. The Legit ASPM platform identifies these issues early – and makes it simple to identify the most impactful fixes, automate remediation, and enact preventative guardrails.
Explore the Legit AI-native ASPM platform with our self-guided demo
Get a quick look at how we secure AI-generated software development.
Frequently Asked Questions
ASPM Proven Performance
-
 Read the Press Releasepress releases
Read the Press Releasepress releasesLegit Named a “Representative Vendor”
For Software Supply Chain Security (SSCS) in the2024 Gartner® Emerging TechImpact Radar: Cloud-NativePlatforms report.
-
 Read the Press Release
Read the Press ReleaseWinner of Seven Cybersecurity Excellence Awards for 2023
Including “Most Innovative Cybersecurity Company” and Gold Awards for Software Supply Chain Security and SDLC Security.
-
 Read the Press Releasepress releases
Read the Press Releasepress releasesLegit Named to Elite “Fortune Cyber 60” List
As an early stage growth cybersecurity company.
Related Resources
-
 Read Nowwhite papers
Read Nowwhite papersMore Coding, Less Remediating
How ASPM Boosts Developer Productivity and the Bottom Line
-
 Read Nowebooks
Read NowebooksA New Approach to Application Security
Download the whitepaper and see how Legit is the new way to manage your application security posture for security, product and compliance teams.
-
 Read Nowwhite papers
Read Nowwhite papersThe Top 6 Unknown SDLC Risks Legit Uncovers
Find out the top unknown SDLC risks we unearth, plus how to prevent them.
-
 Read Nowcase studies
Read Nowcase studiesACV Auctions Uses Legit to Deliver Secure, Continuous Software Innovation
They use Legit Security to help create and maintain a secure and sustainable process for developing new and innovative software.
-
 Read Nowdatasheets
Read NowdatasheetsOverview: Legit Application Security Posture Management
Get an overview of Legit's ASPM capabilities.
-
 Read Nowwhite papers
Read Nowwhite papersLegit 2025 State of Application Risk Report
Get data uncovered by the Legit ASPM platform over the past 18 months.
See More
Related Posts
ASPM Knowledge Base
See Legit ASPM in action
Sign up for a demo, and discover firsthand the full power of the Legit ASPM platform.
Book a demo