Vulnerability Management
Automatically discover, analyze and secure your end-to-end software supply chain.
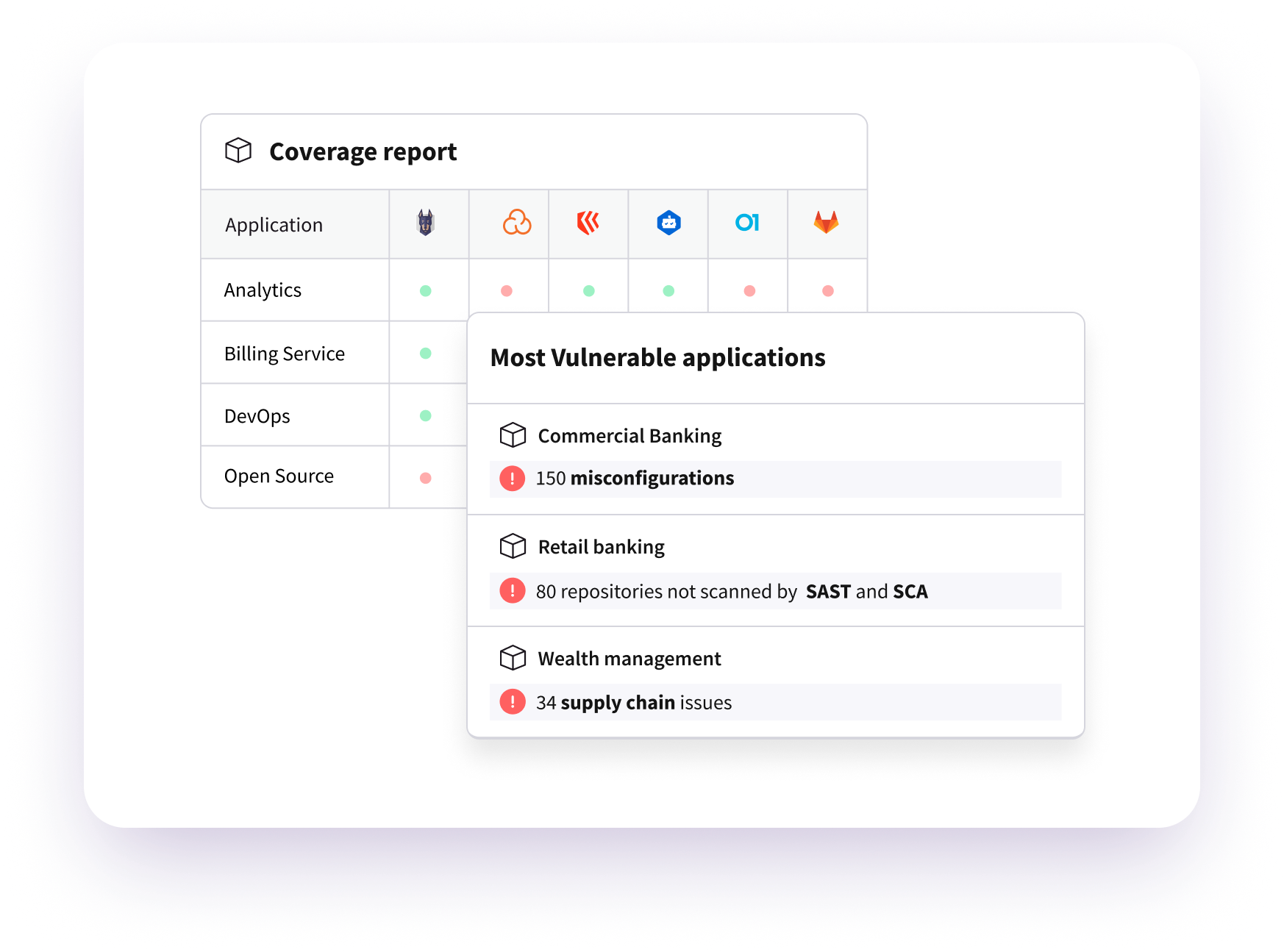
Consolidated Application Risk Management
- Manage application vulnerabilities in one place
- Integrate findings from SAST, SCA, secret scanning and IaC
- Leverage rich context to prioritize and score risk
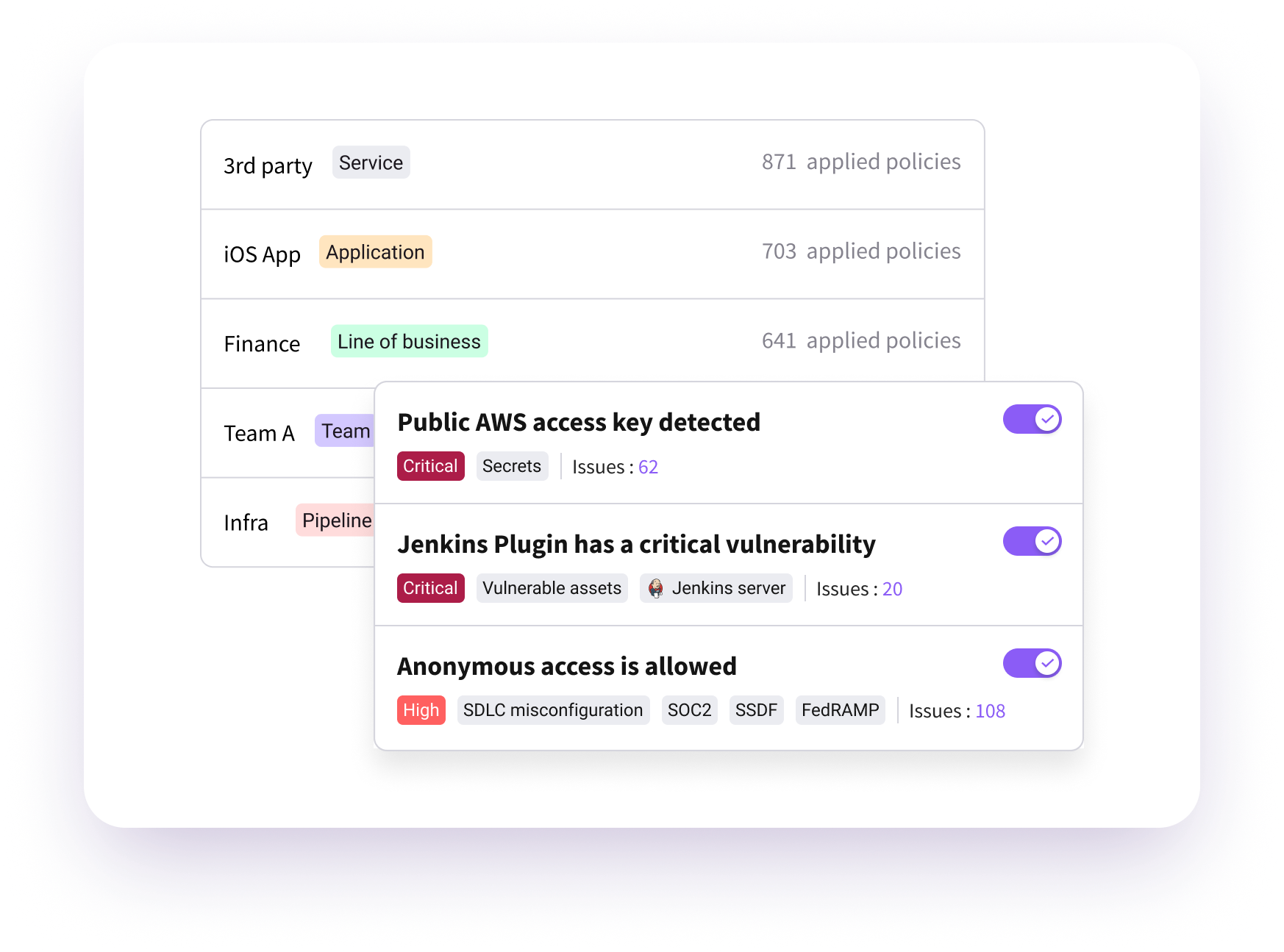
Centralized Security Policy Enforcement
- Centrally manage security policies enforced across your SDLC
- Customize by product lines, teams, pipelines, or individual systems and tools
AppSec Governance And Risk Scoring
- Automated policies to govern application releases
- Enforce security control coverage
- Customize risk scoring to business requirements
- Leverage risk scores for DevSecOps and security champion programs
Automate And Orchestrate Remediation
- Automate remediation and team collaboration
- Orchestrate with ticketing, workflow and productivity tools
- Set policies to automate remediation where appropriate
Related Resources
-
 Read Nowblogs
Read NowblogsTop Vulnerability Management Tools, Tips and Best Practices
In this article, we review vulnerability management, discuss four types of vulnerabilities you should focus on, and provide guidance on best practices to bring your vulnerability management system up to modern standards.
-
 Read Nowblogs
Read NowblogsAn In-Depth Guide to the Vulnerability Management Lifecycle
The vulnerability management lifecycle has become an essential component of an effective cybersecurity strategy within any organization. This lifecycle is a comprehensive and iterative process that involves identifying, evaluating, treating, and reporting on vulnerabilities in systems and software.
-
 Read Nowwhite papers
Read Nowwhite papersMore Coding, Less Remediating
How ASPM Boosts Developer Productivity and the Bottom Line
Blog
Related posts
See More
ASPM Knowledge Base
Request a Demo
Request a demo including the option to analyze your own software supply chain.
Request a Demo