How VibeGuard Secures AI-Generated Code
VibeGuard integrates directly into your IDE and connects to a centralized
management console – securing AI code at the moment it’s created.
Legit is an AI-native ASPM platform that automates AppSec issue discovery, prioritization, and remediation. A trusted ASPM vendor for your AppSec and software supply chain security programs.
AI is revolutionizing development - making it faster, smarter, and more autonomous. It’s also rewriting the rules of application security. Traditional AppSec tools weren’t designed for AI-driven dev processes. Legit is here to help.
Legit is an AI-native ASPM platform that automates AppSec issue discovery, prioritization, and remediation. A trusted ASPM vendor for your AppSec and software supply chain security programs.
AI is revolutionizing development - making it faster, smarter, and more autonomous. It’s also rewriting the rules of application security. Traditional AppSec tools weren’t designed for AI-driven dev processes. Legit is here to help.
Legit VibeGuard is Application Security for AI-led development. VibeGuard prevents vulnerabilities, secrets and risk at the developer endpoint – where AI code is generated. No workflow changes, no slowdowns.
• Blocks issues in your AI IDE before commit
• Integrates with Cursor, GitHub Copilot and other AI code assistants
• Deploy in minutes, see immediate results
• Purpose-built for AI assistants, vibe coding and agentic workflows


VibeGuard integrates directly into your IDE and connects to a centralized
management console – securing AI code at the moment it’s created.
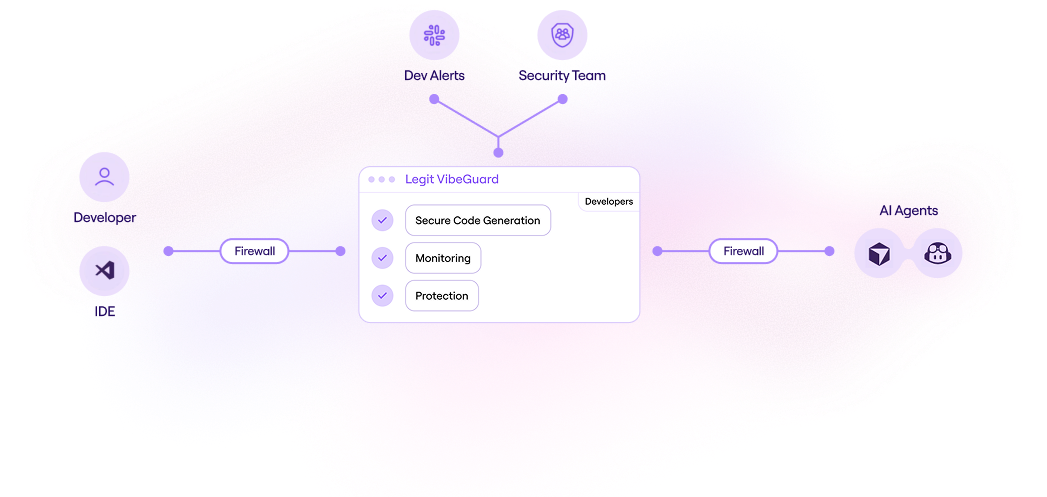
VibeGuard scans AI-generated code for vulnerabilities before it leaves your IDE. Automatically detect secrets, issues and policy violations in real-time as developers code.
Discover every AI model, code assistant, MCP server and AI-generated code across your developer environment. View what’s in active use, evaluate reputation scores and decide to approve, block or flag for review.
Set policy- based controls that prevent code leaks, restrict access and block unsafe AI configurations. Guide AI agents with security instruction files that enforce secure-coding practices.
Define and enforce what systems and data AI coding agents can access. Restrict access to files that commonly contain secrets or credentials to prevent sensitive data from exposure during code creation.
VibeGuard provides complete visibility and security for AI code and development processes. Legit ASPM extends that protection across your entire SDLC – unifying AppSec testing, secrets prevention, software supply chain security and vulnerability management in a unified control plane.
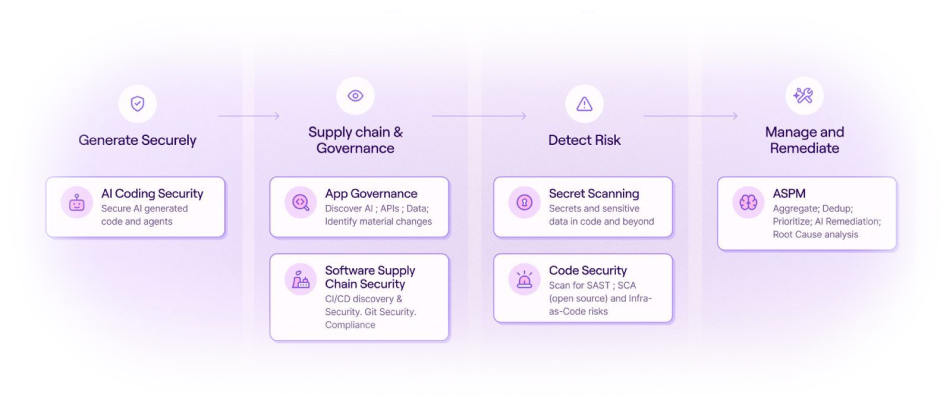
From AI code assistants to agents to MCP servers, get visibility and control over every AI tool across development. Prevent issues in real-time at the source while enabling
developers to move fast.
Stop drowning in alerts from disconnected scanners. Legit consolidates, de-duplicates and prioritizes results from your existing AST tools – or use our native SAST and SCA – into a single prioritized view of what actually matters.
Uncover exposed secrets across your entire dev environment, including source code, Git history, ticketing systems, artifact registries and shared workspaces. Remediate risky secrets and prevent future issues with automated guardrails.
Discover shadow dev assets, track material code changes and enforce policies from code to cloud. Know what's deployed, where vulnerabilities exist and which issues pose real business risk.
Reduce vulnerability noise with AI-powered prioritization that understands business context. Automate discovery, triage and remediation so teams focus on critical risks.
Automate compliance reporting, generate SBOMs and demonstrate your application security posture to auditors, executives and the Board. Meet regulatory requirements without slowing down development.
Traditional ASPM tools struggle with AI-generated code, disconnected toolchains and overwhelming alert volumes. Legit’s
AI-native platform was built from the ground up to handle the complexity of modern, AI-driven software development.
Unlike traditional ASPM tools that rely on basic severity scores, Legit uses AI to understand application context, business criticality and code relationships. This means better prioritization, fewer false positives, and remediation guidance that actually makes sense for your business.
Most ASPM platforms only see what’s in your CI/CD pipeline. Legit starts at the developer endpoint where AI code is generated and extends through production. Catch issues before they’re committed and discover shadow AI tools developers are using.
Legit integrates with your existing AST tools or provides enterprise-grade native SAST, SCA and secrets scanning. We also integrate with your broader tech stack including cloud and API security, identity management, bug bounty programs and more. We consolidate, de-duplicate, and prioritize findings across all your tools without vendor lock-in.
Our AI agents suggest specific code fixes, create tickets with full context and track remediation through to validation. Developers get actionable guidance. Security teams get metrics on actual risk reduction. Vulnerabilities get fixed 10x faster.
AI is completely changing the face of development, and AI-driven development introduces more risk than we’ve ever seen. Legit’s AI-native AppSec capabilities enable your developers to work in the tools they know and love without sacrificing your business’ application security posture.



Stop worrying about what you’re missing – from GenAI code to secrets - and understand the holistic risk across your entire software factory and attack surface. Make sense of findings from multiple AppSec tools to confidently prioritize and fix highest-risk issues fast.
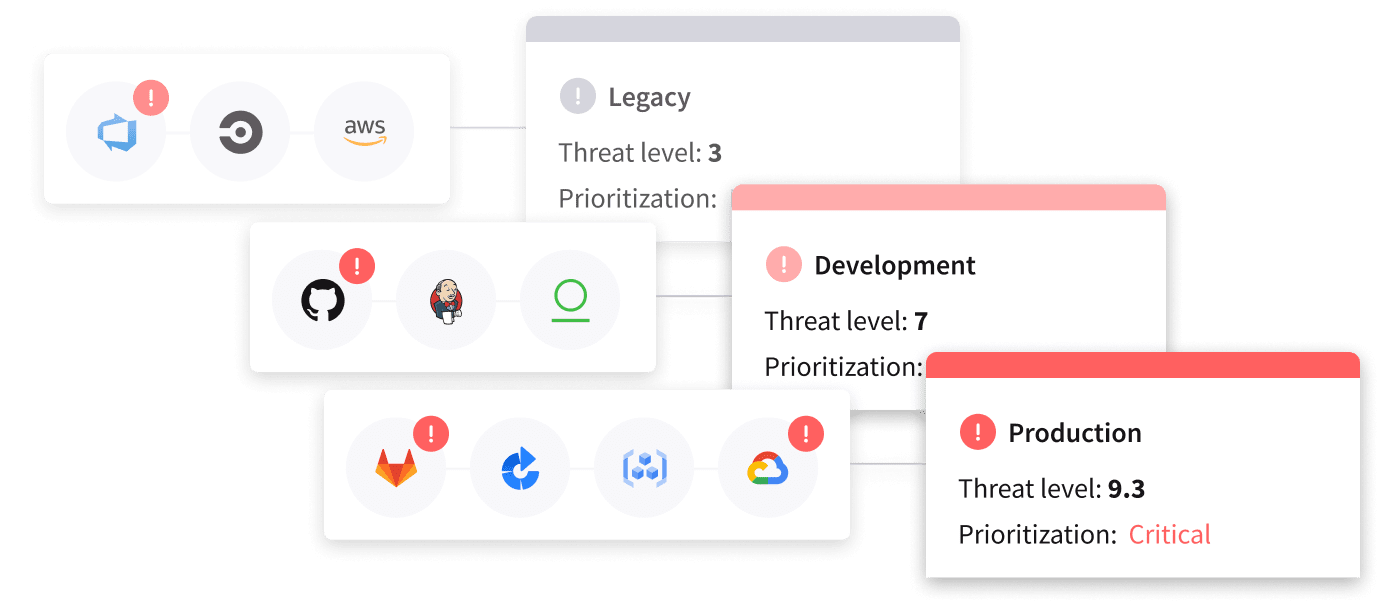
Implement in no time to lighten the load on your security teams by consolidating findings from multiple tools and setting boundaries that let developers work their own way safely. Create processes that engage developers to get cleaner code the first time and use complete context to prioritize fixes.
Test your policies, ensure they’re being enforced, and show the value of your hard work. Collaborate and hold everyone accountable with data. Use metrics to communicate more clearly about risk and progress with developers, product teams and executives.

This capability provides automated, holistic vulnerability management that discovers assets across the SDLC, identifies and prioritizes security gaps, orchestrates remediation workflows, integrates with ticketing tools, and continuously reports on risk metrics - helping teams efficiently surface and fix critical vulnerabilities across code, infrastructure, and dependencies.

Legit’s SCA and SAST go beyond legacy scanning with precise reachability analysis, AI vulnerability detection, and license risk enforcement. By reducing false positives and delivering context-aware insights, security and development teams can prioritize real threats, streamline remediation, and more effectively secure modern, AI-driven applications.

Legit delivers the most accurate AI-powered secrets detection, prevention, and remediation across your software development lifecycle. By scanning beyond source code, including Git history, build logs, and shared workspaces like Slack, Teams, Confluence, and Jira, Legit eliminates secret sprawl, enforces policies, and prevents leaks before they become security or compliance incidents.

Legit provides automated end-to-end software supply chain protection by discovering and mapping your entire SDLC; continuously inventorying assets and security controls; enforcing hundreds of policies; scanning for vulnerabilities, misconfigurations and secrets; and surfacing risks for remediation – all integrated seamlessly with existing development pipelines.

Gain deep visibility and intelligent automation for material changes across the software development lifecycle. By combining code-level analysis with workflow orchestration, Legit enables AppSec and development teams to proactively detect, assess, and remediate security-impacting changes before they reach production.

Legit’s intelligent, AI-powered
application context allows you to
prioritize and act fast based on
vulnerabilities and issues that present the most significant business risk.
Legit enables development teams to safely and securely leverage AI code assistants and AI-generated code. And by reducing vulnerability noise, Legit allows developers to prioritize only remediation that matters.
Legit provides visibility and context to understand risk throughout development. We help you understand where secrets, dependencies, and misconfigurations exist, and when, where, and how AI code is employed.
key features & capabilities
Legit integrates with all the systems and AppSec test tools used to build and deploy your applications. From development to testing to production, Legit provides a central view of all vulnerabilities, misconfigurations, and other issues that drive up application risk.
Legit orchestrates AST scanning and correlates/de-duplicates data to help you identify exactly where actions can have the most material impact on risk reduction.
Legit integrates with the systems your developers use to do their jobs to automate and speed remediation.
Legit enables teams to get proactive with preventing future issues. By automating processes to enforce guardrails and policy, Legit positions teams to benefit from repeatability and elimination of significant manual effort.
With the Legit Score, you can pinpoint the issues that create the greatest business risk based on the context of the application and your priorities. We go well beyond CVSS scores and simple severity rules to fully contextualize – and prioritize – issues for remediation.
Through deep discovery capabilities, Legit builds a comprehensive inventory of all your API endpoints. By analyzing the role of the API and any associated issues, we can help you quickly identify and remediate any issues uncovered.
Understanding changes in an application is key to managing your overall AppSec posture. By continually discovering all elements of an application and the software development environment, Legit can alert you to changes that elevate your AppSec risk.
As developers harness the power of AI and large language models (LLMs) to develop and deploy capabilities more quickly, new risks arise. Through Legit, you can get a full view of code derived from AI tools (e.g., Copilot), enforce policies, and enact preventative guardrails to stop future vulnerabilities.
Within continuous and automated SDLC discovery, Legit enables you to visualize the entire software factory and key dependencies. Legit also helps you identify shadow assets and changes that present risk to your applications.
Key to both security and compliance is having a clear understanding of all elements and dependencies associated with an application. Through Legit, you can create and export comprehensive SBOMs to support security and compliance requirements.
Legit delivers comprehensive data and reports to assess the state of your AppSec program and to communicate both challenges and improvements with internal and external stakeholders. Reporting supports a wide array of compliance and audit requirements.
Legit enables you to set, monitor, and report on policy compliance across disparate security teams. By setting consistent standards, you can ensure testing and remediation are prioritized regardless of the dev team or toolset, and that an audit trail can be produced for attestation.
Hear how Ricardo Lafosse, CISO at Kraft-Heinz, uses Legit Security to collaborate with dev teams and remediate application security issues early in the pre-production development environment.

Legit integrates with all the systems and AppSec test tools used to build and deploy your applications. From development to testing to production, Legit provides a central view of all vulnerabilities, misconfigurations, and other issues that drive up application risk.

Legit orchestrates AST scanning and correlates/de-duplicates data to help you identify exactly where actions can have the most material impact on risk reduction.
Legit integrates with the systems your developers use to do their jobs to automate and speed remediation.

Legit enables teams to get proactive with preventing future issues. By automating processes to enforce guardrails and policy, Legit positions teams to benefit from repeatability and elimination of significant manual effort.

With the Legit Score, you can pinpoint the issues that create the greatest business risk based on the context of the application and your priorities. We go well beyond CVSS scores and simple severity rules to fully contextualize – and prioritize – issues for remediation.

Through deep discovery capabilities, Legit builds a comprehensive inventory of all your API endpoints. By analyzing the role of the API and any associated issues, we can help you quickly identify and remediate any issues uncovered.

Understanding changes in an application is key to managing your overall AppSec posture. By continually discovering all elements of an application and the software development environment, Legit can alert you to changes that elevate your AppSec risk.

As developers harness the power of AI and large language models (LLMs) to develop and deploy capabilities more quickly, new risks arise. Through Legit, you can get a full view of code derived from AI tools (e.g., Copilot), enforce policies, and enact preventative guardrails to stop future vulnerabilities.

Within continuous and automated SDLC discovery, Legit enables you to visualize the entire software factory and key dependencies. Legit also helps you identify shadow assets and changes that present risk to your applications.

Key to both security and compliance is having a clear understanding of all elements and dependencies associated with an application. Through Legit, you can create and export comprehensive SBOMs to support security and compliance requirements.

Legit delivers comprehensive data and reports to assess the state of your AppSec program and to communicate both challenges and improvements with internal and external stakeholders. Reporting supports a wide array of compliance and audit requirements.

Legit enables you to set, monitor, and report on policy compliance across disparate security teams. By setting consistent standards, you can ensure testing and remediation are prioritized regardless of the dev team or toolset, and that an audit trail can be produced for attestation.
You can’t secure what you can’t see. Legit eliminates visibility gaps, unifying security visibility across the entire development environment — automatically. Discover, fix, and prevent data leakage in minutes for everything from shadow IT to secrets and source code to developer use of risky LLMs and GenAI.
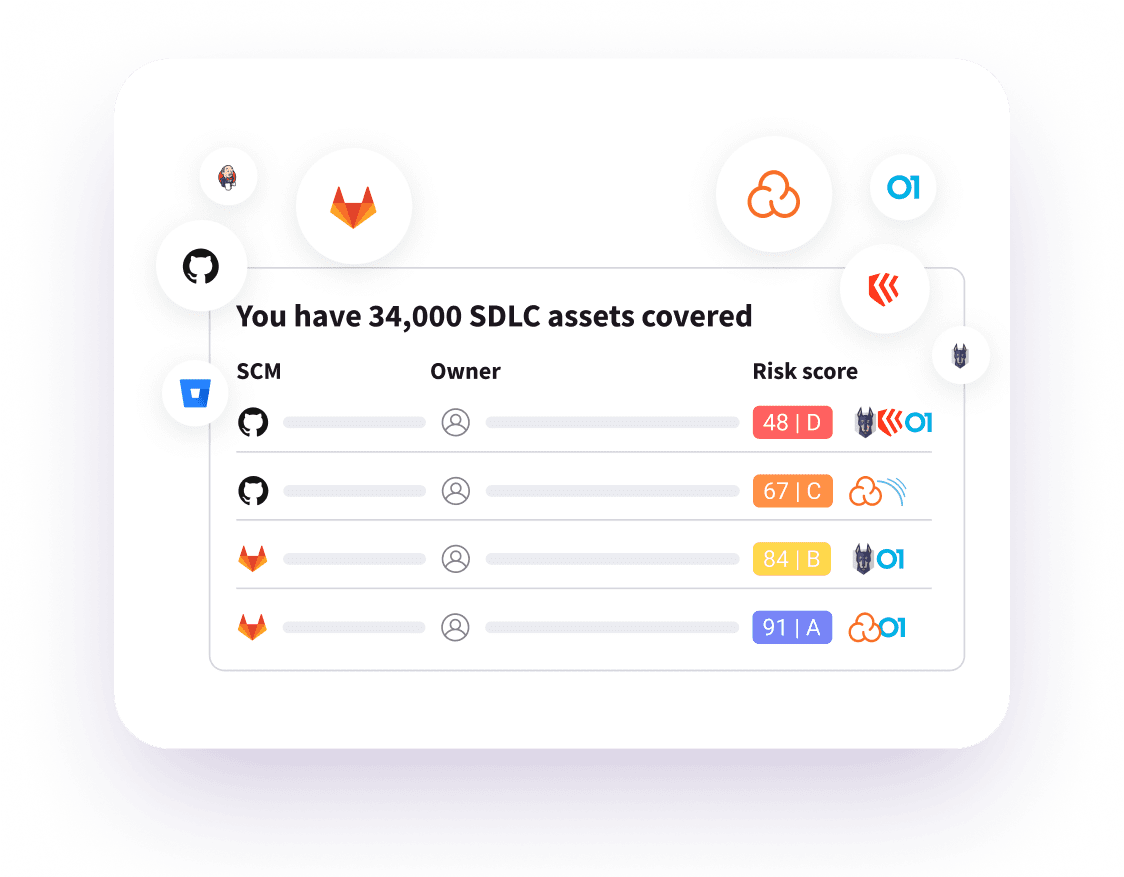
Avoid alert fatigue and focus on the critical vulnerabilities that matter. Legit turns alert confusion into clarity by prioritizing the risks with the greatest potential impact to disrupt your business — keeping analysts productive and your business secure.
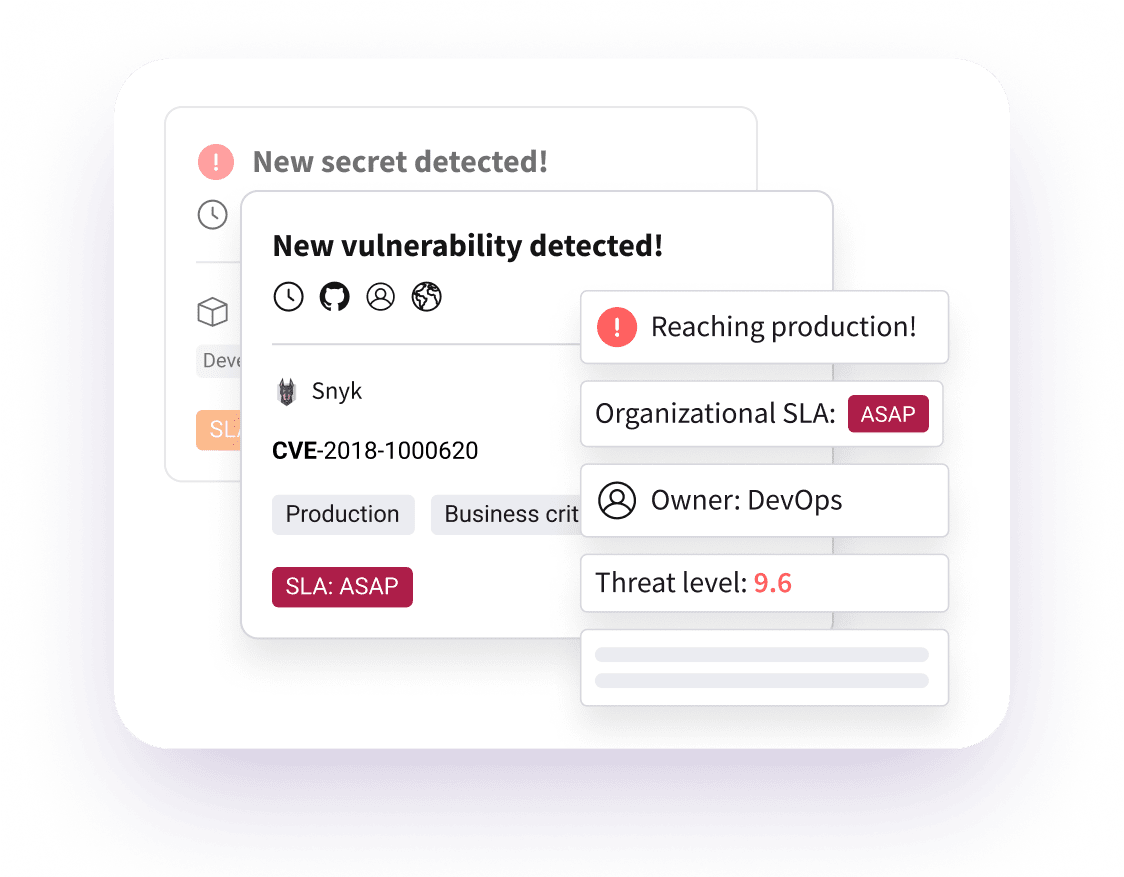
Your software factory is in a constant state of change – and demands from auditors and compliance teams aren’t letting up. New assets, tools and technologies are regularly introduced, and security simply cannot keep up. Use Legit to automate time-sucking tasks and deliver real-time validation and evidence into your daily development and application security operations. Know what exists, if it’s secure, and how and when to act — any time, all the time.
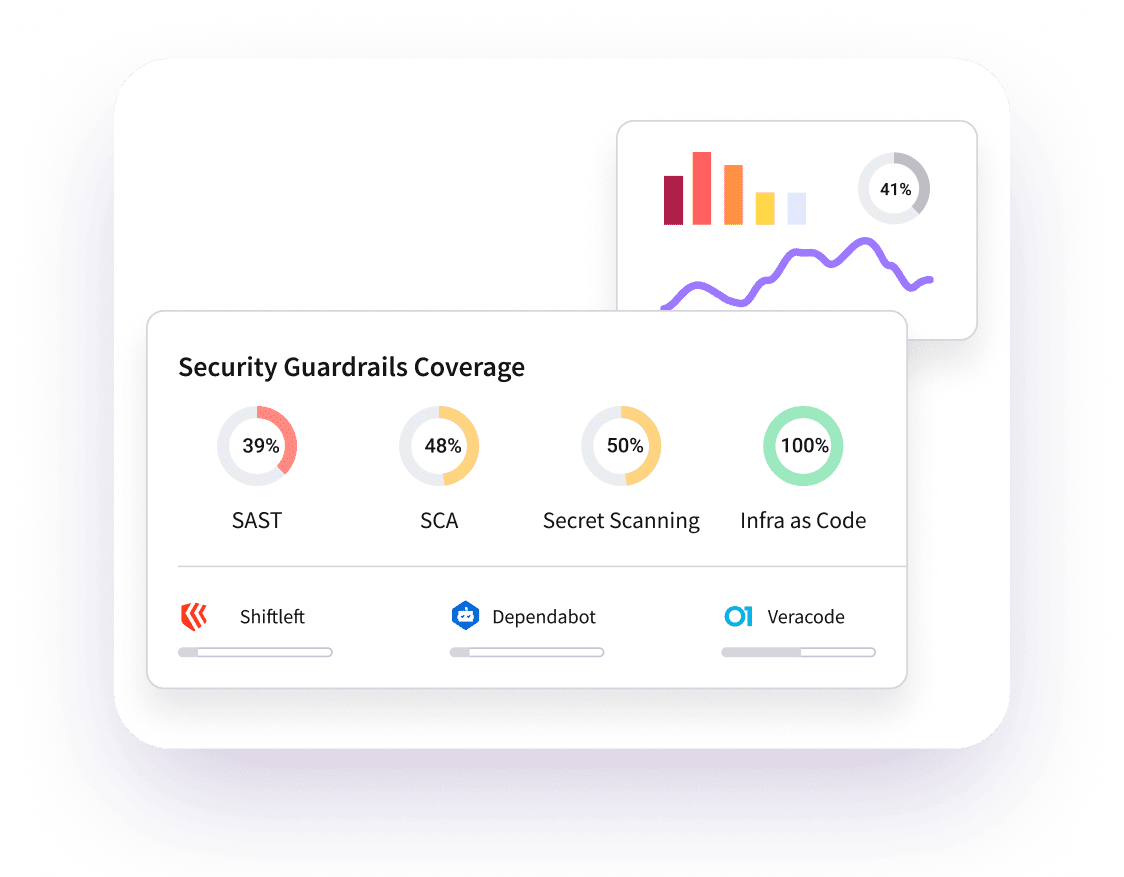
Advanced AI, LLMs, and automation have powered the Legit platform since day 1. With AI-driven correlation and prioritization, and innovative AI model detection, security teams are equipped with the modern tools, techniques, and guardrails to accelerate AI development while mitigating its risks.

Understand how ASPM creates a foundation that makes your AppSec activities more effective and efficient.
.jpg?width=2000&height=1045&name=Blog-Image-Reality%20Check%20on%20Securing%20AI-Generated%20Code-2%20(1).jpg)
We surveyed 117 security professionals to understand their priorities, plans, and pains surrounding AI-led software development.

Get details on the new AppSec requirements when AI writes code.

.png)

Learn how AI compliance helps organizations streamline regulations, reduce risk, and leverage AI to monitor, report, and maintain compliance efficiently.

Learn about the differences and similarities between SASE and ZTNA, and discover how together they deliver secure access across cloud-native environments.

Learn about the similarities and differences between SSE versus SASE. Understand how they work so you can choose a solution to protect your business.

Mar 18, 2026
Webinar
Click below to read more and register for the webinar
View More
Mar 24, 2026
San Francisco, CA
See more details about the breakfast panel and networking session in San Francisco, CA.
View MoreGet a stronger AppSec foundation you can trust and prove it’s doing the job right.
Request a Demo