Advanced Code Change Management & Protection
AI‑driven visibility, automated security checks, and preventative guardrails stop risky code changes from reaching production - without slowing developers or delaying releases.
Stopping Unmanaged Code Changes in Their Tracks
Modern applications undergo thousands of code and configuration changes every week, and many can introduce real security risks. Whether introduced by a human or an AI coding tool, not all changes are equal. Understanding and managing these changes is critical. Legit’s AI-powered capabilities automate the detection, assessment, and remediation of code changes to help you maintain a strong AppSec posture.
High-risk changes get buried under mountains of routine commits
Manual code reviews don’t scale for the speed of modern development
Alert fatigue from false positives slows teams down and creates friction
Missed changes introduce gaps that compromise your AppSec and compliance postures
You can reduce risk from code changes by
Pinpointing high-risk changes
Ensure your team has visibility into changes that may have a material impact on your security posture
Automating code change detection
Apply AI to automate the identification of code changes that present risk
Enacting guardrails and prevention
Put policies and automated guardrails in place to ensure code changes are managed securely
Standardizing the change process
Apply consistent change control processes to code to prevent high-risk issues from hitting production
Key Features of Legit Advanced Code Change Management
Risky Code Change Detection
Legit identifies all code changes across your development environment and leverages AI to highlight any change that may adversely impact your security posture.
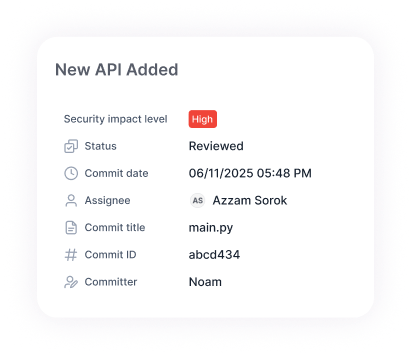
Context for Smart Decision-Making
Legit delivers a comprehensive view of your development environment and uses this context to ensure developers focus on mitigating risk where it matters – rather than chasing every change-related alert and ticket.
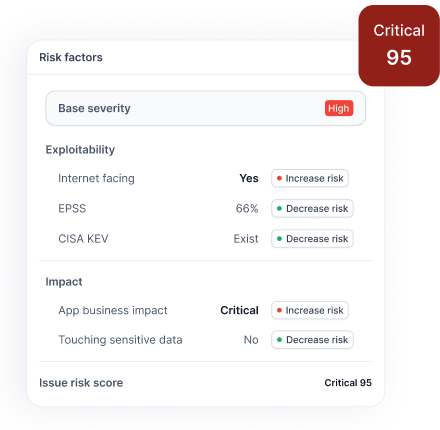
Automated Security Reviews & Remediation Workflows
Legit enables you to establish consistent workflows for developers so risky changes are addressed as defined by your organization’s security and compliance policies. You can also put clear and automated security reviews in place, based on policy, for high-risk changes.
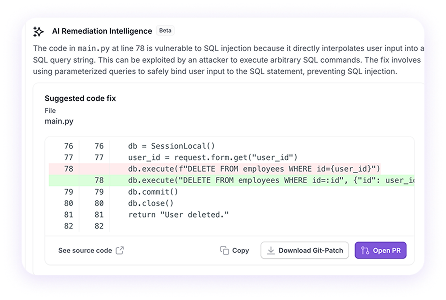
Preventative Guardrails
Legit is designed with prevention in mind. The platform enables you to establish clear guardrails for code changes and allows you to automatically enforce the guardrails to drive consistent security.
AI-Powered Accuracy
Legit leverages AI to deliver you the most accurate results. With low false positives, we help you ensure your developers spend their time on the issues that matter to your security posture without wasting time and resources.
How Do Risky Changes Slip By?
Inadvertent risky edits in code or configs
Temporary shortcuts or overlooked changes to auth/crypto/data controls

Third‑party & dependency updates
Transitive changes alter security posture without direct code edits

Misconfigurations in pipelines & IaC
Build logs, runners, and IaC defaults introduce exploitable paths

Privilege & permission changes
Role/ownership edits expand access beyond least‑privilege

AI code bypasses security
AI-generated code merged without full context or understanding of embedded logic without security review

Secrets exposure
Secrets accidentally committed by developers or AI code assistance
Frequently Asked Questions
Related Resources
-
 Read Nowwhite papers
Read Nowwhite papersThe Top 6 Unknown SDLC Risks Legit Uncovers
Find out the top unknown SDLC risks we unearth, plus how to prevent them.
-
 Read Nowwhite papers
Read Nowwhite papersAppSec in the Age of AI
Understand the new AppSec requirements when AI writes code.
-
 Read Nowwhite papers
Read Nowwhite papersMore Coding, Less Remediating: How ASPM Boosts Developer Productivity and the Bottom Line
Understand how ASPM makes your development process more efficient and effective.
See More
Related Posts
ASPM Knowledge Base
Request a Demo
Request a demo including the option to analyze your own software supply chain.
Request a Demo