Blogs about CISO




Strengthening Software Security Under the EU Cyber Resilience Act: A High-Level Guide for Security Leaders and CISOs
Get guidance on key tenets of the EU CRA and how Legit can help address them.
Read More.png?width=740&height=220&name=Legit-NewAICapabilities-2%20(1).png)
.png?width=740&height=220&name=ASPM_1200x627%20(2).png)


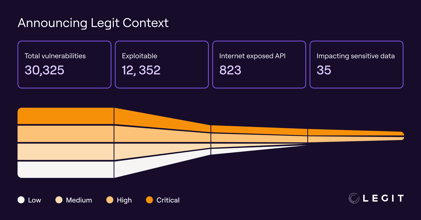
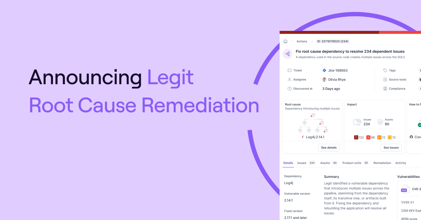

.png?width=740&height=220&name=Blog%20Thumbnail%20(1).png)
White House Executive Order: Strengthening and Promoting Innovation in the Nation’s Cybersecurity
Get details on this new cybersecurity Executive Order and its implications.
Read More
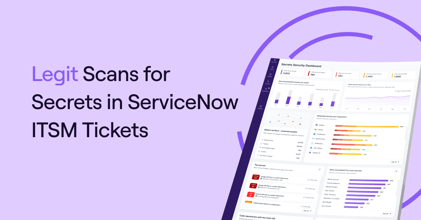


How to Reduce Risk From Exposed Secrets
Understand how secrets end up exposed, and how to prevent this risk.
Read More
Unlocking the Power and Potential of GenAI in Software Development
GenAI's rapid adoption brings with it significant challenges in security, governance, and visibility.
Read More
How to Reduce Risk From Developer Permissions Sprawl
How to Reduce Risk From Developer Permissions Sprawl. Get steps to prevent risky permissions sprawl in your SDLC.
Read More
How to Reduce Risk From Misconfigured Build Assets
How to Reduce Risk From Misconfigured Build Assets. Get steps to prevent risky misconfigurations in your SDLC.
Read More
Software Security Best Practices: Where to Focus First
Software Security Best Practices: Where to Focus First. Get our recommendations on where to focus your software security efforts.
Read More
How to Mitigate the Risk of GitHub Actions
How to Mitigate the Risk of GitHub Actions. Get highlights of our research into the security of GitHub Actions, and our advice on mitigating the risk.
Read More
ESG Survey Report Finds AI, Secrets, and Misconfigurations Plague AppSec Teams
ESG Survey Report Finds AI, Secrets, and Misconfigurations Plague AppSec Teams. Find out how your peers are managing application security challenges.
Read More
Why Legit Security Immediately Joined the New Coalition for Secure Artificial Intelligence (CoSAI)
Why Legit Security Immediately Joined Google’s New Coalition for Secure Artificial Intelligence (CoSAI). Get details on CoSAI and why Legit chose to be a part of this forum.
Read More
Security of Custom GitHub Actions
Security of Custom GitHub Actions. Get details on Legit's research on the security of custom GitHub Actions.
Read More
Announcing The State of GitHub Actions Security Report
Announcing the State of GitHub Actions Security Report. Get details on Legit's research on the security of GitHub Actions.
Read More
EU Cyber Resilience Act: Updates and Important Requirements
Ensure compliance with the EU Cyber Resilience Act. Learn CRA essentials, how to secure digital products, and how Legit Security helps automate compliance and risk management.
Read More
What is ASPM? Application Security Posture Management 101
Learn how Legit Security enhances Application Security Posture Management (ASPM) by automating key processes to ensure business protection.
Read More
Securing the Vault: ASPM's Role in Financial Software Protection
Discover the importance of Application Security Posture Management (ASPM) in financial software protection. Learn how ASPM enhances security practices and compliance in the U.S. financial services sector through Legit Security.
Read More
2023 Predictions for Modern Application Security
This blog analyzes trends in application security and predicts the future direction of enterprise application security programs.
Read More
Modern AppSec Requires Extending Beyond SCA and SAST
Examining the evolution of application security and why securing the modern SDLC requires organizations to embrace new approaches to supply chain security.
Read More
Integrating Security into DevOps: A Step-By-Step Guide
If you haven’t already been integrating security into DevOps, now’s the time. Learn about the benefits & use this 4-step guide to secure your DevOps.
Read More
Software Supply Chain Risks to Be Aware of
Discover four key supply chain risks every CISO must address as software technology evolves and security becomes crucial.
Read More
10 Agile Software Development Security Concerns You Need to Know
Agile development methodology has become increasingly popular, but it doesn’t come without security concerns. Get to know the top 10 agile software development security concerns you face.
Read More
How to Secure Your Software Supply Chain in 10 Steps
Create a Secure Software Supply Chain in 10 Easy Steps In today’s age of security breaches, it’s more important than ever to create a secure software supply chain. Follow these 10 easy steps to keep your business safe.
Read More
Secure Software Development Lifecycle (SDLC): Key Phases Guide
Explore how to seamlessly integrate security into SDLC phases, transforming your development process to achieve enhanced protection and resilience.
Read More.jpg?width=740&height=220&name=security%20camera%20example%20(2).jpg)
Request a Demo
Request a demo including the option to analyze your own software supply chain.
