SDLC (Software Development Life Cycle) is a breakdown of all the stages involved in software creation. There are distinct SDLC stages and many different software development models in use. Security should be integral to each step along the way to ensure that the resulting product is secure. We’ll cover the fundamentals of a secure SDLC and explain why “shifting security left” can also save time and expense and prevent the accumulation of errors and vulnerabilities from previous stages.
There are several SDLC models -
- Waterfall model
- V-shaped model
- Iterative model
- Spiral model
- Big bang model
- Agile model
While these models are different in their implementation, they all consist of the same lifecycle:
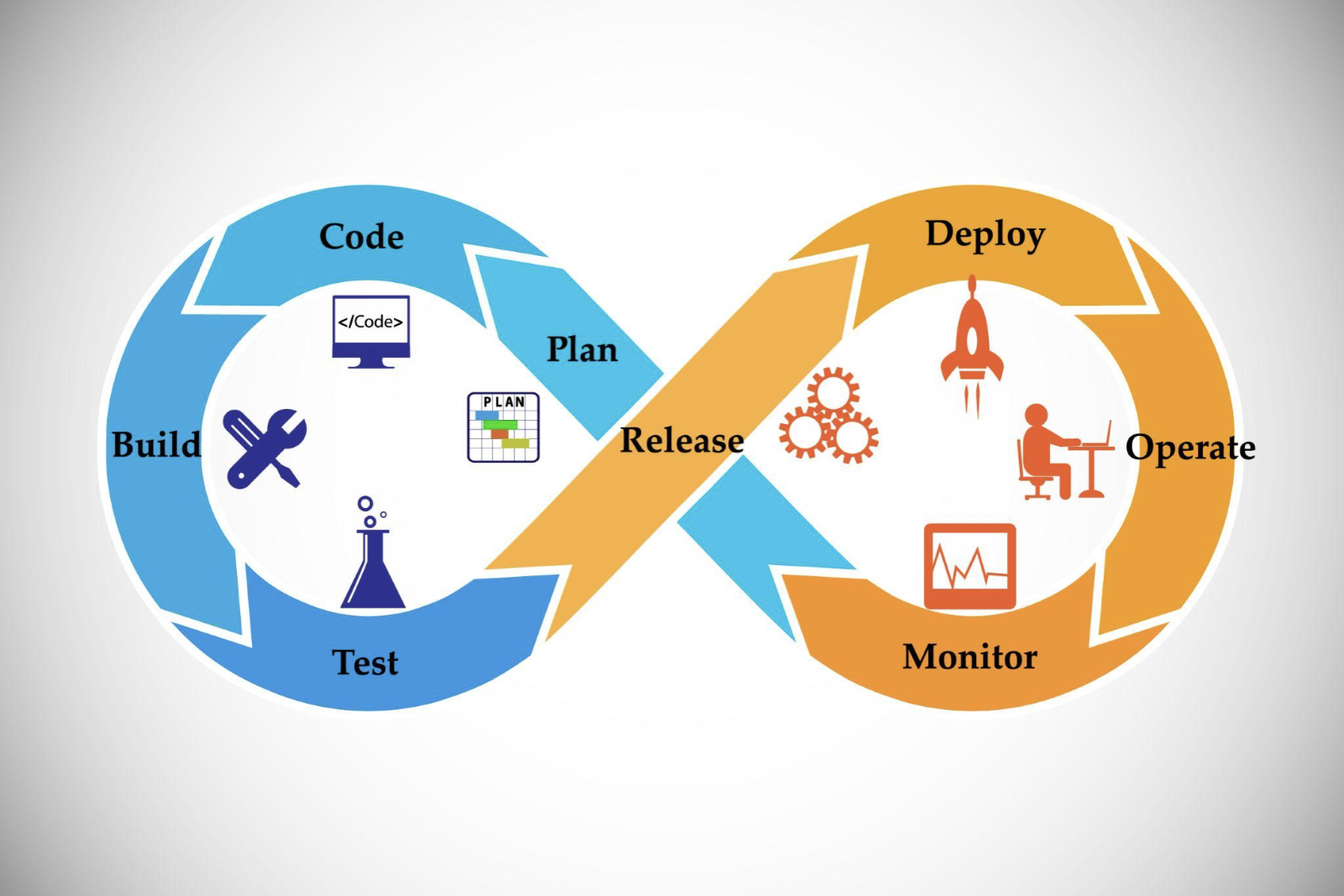
- Requirements phase - getting the feature requirements.
- Design phase - technical design of the requirements.
- Planning testing procedures.
- Developing phase - writing the code that implements the requirements and design.
- Testing phase - validating that the desired functionality is working as expected.
- Release and maintenance phase - releasing the new functionality and supporting it.
Not securing every step mentioned above can result in accumulating errors from the previous steps — increasing the possibility of an attack, and requiring costly solutions. In the past, security-related activities were performed in the testing phase; however, security validations were often completely neglected due to time limitations.
This led to time-consuming and expensive work stoppages to address immediate issues and plan additional fixes in a second round of the SDLC. A secure software development life cycle (SSDLC) ensures the protection of every step along the way — resulting in a secure outcome.
- While planning the requirements for the new feature, identify the risks to your organization. This can help you prioritize and address the most significant vulnerabilities before they reach your system.
- Include secure coding standards during development, such as code reviews, code scanning tools, and trustworthy open-source libraries.
How Does SDLC Security Work?

Every software business is prone to security vulnerabilities. As demonstrated by several recent data breaches, and the increased sophistication of hackers, it is increasingly imperative to have a secure SDLC at every stage of development. Securing your software is not an easy task. Security practices must shift left and take priority at every step in the SDLC.
Mastering SDLC security is all about learning how to integrate defensive and offensive security measures into the entire SDLC. As demonstrated above, integrating security actions into every one of the software lifecycle stages requires an understanding of the process needs:
1. The Requirement Phase
The team determines how and where the product is prone to security attacks.
2. The Development Phase
The team maintains risk awareness, adheres to coding best practices, and uses available security frameworks.
Because of a prevailing belief that security practices and testing inhibit the development process, many teams do not consider this approach to their SDLC. This practice is crucial, demonstrated by influential organizations which have proven its efficiency:
Microsoft Security Development Lifecycle was developed to build more secure products and services. It introduced security considerations through all development phases and reduced development costs.
NIST Secure Software Development Framework (SSDF) was created by the National Institute of Standards and Technology (NIST), the organization tasked with tracking publicly known software vulnerabilities, and maintenance of the National Vulnerability Database (NVD).
SSDF defines software development practices based on established practice documents from organizations such as OWASP. Each practice must contain four elements: a unique identifier for the practice and why it’s beneficial, the action needed in order to perform this practice, examples of tools and methods for implementation, and a reference to an established task. This approach helps organizations when prioritizing security activities and resources.
Why a Secure SDLC Matters
As demonstrated above, a secure SDLC is crucial, but what are the consequences if teams do not adhere to security practices?
- Fixing a security-related issue right before a release can be costly. When issues arise, developers who have moved on to other tasks are required to switch contexts and recall “old” code to find the problem and fix it. Time restraints create significant challenges for teams to handle the gap.
- Addressing issues at the last moment can cause delays when trying to release to production. Taking these steps before development can reduce the pressure before release, and increase the accuracy of time estimations.
- Penetration testing is a great way to validate an organization's networks and systems, but post-development testing only detects 50 – 80% of vulnerabilities. For these tests to succeed, developers should know how to “think like a hacker” and prepare for a potential attack before development starts.
- Initial software releases are less secure. If the team does not have a secure SDLC, major breaches can occur, potentially affecting customer loyalty and business reputation.
The benefits of a secure SDLC are extensive. Potential vulnerabilities are easier to detect, cost of development is reduced, and time to production is decreased. When the validation process is a part of the regular SDLC, it is easier for developers to perform security testing, increasing efficiency.
The initial purpose of NIST CSF was to help secure the United States’ critical infrastructure. However, we can more clearly see that this framework is relevant to any and all organizations that need to secure their operating environment from a broad range of cybercriminals. In the past, security was traditionally considered at the end of the Software Development Lifecycle (SDLC). Today’s increasingly hostile cybersecurity environments along with businesses’ increased dependence on digital services demand that organizations also put the utmost attention on security across the pre-production development environment and SDLC by abiding to an IT security framework such as NIST CSF. As previously mentioned, the Protect, Detect, and Respond operating model is a pillar of this framework. It should be the motto by which any organization that wishes to protect itself from cybersecurity threats, creates its cyber security plan.
5 Tips & Best Practices for a Secure SDLC
A software product, even a flawless one, cannot be released until it’s proven to be highly secure. Effective security protocols don’t appear instantly. It requires significant effort to embed them inside the current lifecycle, validating that each phase has the required security measures.
Using the following SDLC best practices, you can learn how to integrate them into your system.
1. Update Security Requirements to Stay Current
This is the first stage in the SDLC process. Developers and security experts decide what are the most important aspects to handle during the upcoming software lifecycle.
It is very important to adjust the new requirements to the application, to see if some of the new rules are already supported, or to see what needs to be added.
Analyzing the main security risks at the very first stage of development helps decide which security requirements should be taken into mind.
The risks should be presented clearly, for them to be easy to implement.
Consider the following scenario:
A new endpoint was added to a product that stores customers' data. The endpoint was meant to return some metadata values, but instead returned non-encrypted personal customer data. If this issue was addressed at the very beginning of the feature planning, and a new security requirement regarding handling and encrypting personal data was presented - this malfunction could have been avoided. Security requirements are derived from past vulnerabilities and current standards. They help implement new features and improve existing ones.
This assessment should be done consistently in order to keep the application highly secure. A great way to define these requirements is by using OWASP ASVS - a catalog of available security requirements. Making these updates ensures your software stays protected from current threats.
2. Don’t Lose Focus on DevSecOps
DevSecOps stands for Development, Security, and Operations. It’s an integration of DevOps and security - by addressing issues that arise from CI / CD (Continuous Integration/Continuous Development) pipelines.
In the past, security roles were designated to a separate team. Today, security is integrated into every part of the SDLC, among all teams. Access to infrastructure should be controlled by security manners. This means keeping security measures in mind, such as secured configuration parameters. With DevSecOps - these controls can be applied automatically according to the team's requirements.
What should be automated? Each organization should look at its development and operations environment - monitoring, APIs, CI / CD pipelines - and incorporate automation technologies into it. In addition to automation - scaling should be kept in mind. Recent cloud native technologies such as containers and microservices help many organizations in designing, building, and running applications, but they should be aligned with the appropriate security guidelines.
Once security manners such as secured containers, secured APIs, encrypted data between microservices, and security testing is in the CI process - the application is safely secured.
3. Set Up Secure Design Requirements & Protocols
This might be one of the easiest ways to implement SSDLC, and one of the most important SDLC best practices. How can these protocols get addressed? When starting to design the software and infrastructure, design requirements and protocols should be planned, with the help of security experts and architects. Once the plan has been developed, security standardization gets implemented inside the organization.
Planning out security protocols keeps the entire lifecycle consistent. When the goals are clear - it’s easier for the different teams to implement them during the SDLC process.
These protocols are great to use as a reminder during the development phase. It keeps everyone on track, helps add and implement planned security requirements, and keeps everyone on the same page.
Design requirements should be strict, and address your organization's needs. For example — one can define a requirement that every code review needs at least 3 reviewers, but this can block the development process. In that case, the requirement should be defined again and get adjusted to the right needs — to benefit security and agility.
These protocols are reviewed by contributors in the organization before implementing them. In that way, they will be woven seamlessly into the organization, which will make it easy to start implementing these requirements.
4. Stay Prepared with a Standard Incident Response
Writing down each threat out there is great - but what happens when the complexity of the code is growing, the software evolves, and there are threats that no one thought about? Being one step ahead of security threats isn’t enough. A well-prepared incident response plan can save the day.
Incident Response Plan (IRP), or Incident Management Plan (IMP) is a set of tools used to detect, remove, and remediate attacks. It ensures a quick response when an actual security attack happens. Lack of IRP can cause severe damages that are difficult to recover from, such as data loss and long downtime.
To keep this process effective, there must be a dedicated team (the “incident response team”) for managing plans and analyzing any security event that occurs. It contains security analysts, researchers, and legal advisors to address every incident. This team is the first one to contact in case there is a breach.
An IRP is an important part of a security-driven development process. It helps track the root causes of past incidents — which helps learn how to avoid the same security threat in the future. Downtime and any other damage that an incident can cause are handled quickly and efficiently, without shutting down the system and causing negative outcomes. It helps our SDLC overcome security attacks.
5. Use Threat Modeling to Your Advantage

If you can’t beat them… join them.
The best way to know how to avoid attacks - is to know how and when the next strike will come.
A threat model includes all the information that can affect security. It can be applied to software, applications, systems, and networks. These kinds of models help recognize what can go wrong and what should get fixed. It’s not a substitute for penetration testing and code reviews (and vice versa) - tests and code reviews are meant to find bugs in the code, while threat modeling helps in finding bugs in design.
Threat modeling helps look at software like a potential hacker. During this process, organizations analyze the system, which helps find some caveats and understand the system better. This process is conducted in the design phase to handle design flaws in the early stages of the software lifecycle, but it can work on other stages as well.
There are numerous ways a threat model can help software lifecycle:
- Detect problems in early stages of SDLC (before development)
- Identify new security requirements
- Fix security gaps before software release
- Detect vulnerable locations inside the application
One of the best SDLC practices is knowing what can hurt the system, and avoiding it instead of handling a live attack — saving time and money as a result.
Invest in SDLC Security with Help from the Experts
Creating a secure SDLC is a must. Not doing so can hurt an entire organization - starting from data breaches, sensitive information leakage, system downtime, and customer loss.
SSDLC treats development and security as a single process and is very important in software development. Everything is secured and protected using SDLC best practices - planning security requirements, threat modeling, and incident response process.
When your SDLC needs a little boost - ask the experts for help. Legit security makes the best effort in securing your SDLC. Contact us if you would like to know some more!
Download our new whitepaper.


