A popular vendor of Magento-Wordpress plug-ins/integrations with over 200,000 downloads, has been hacked. This recent attack is a reminder that malicious 3rd party plug-ins/integrations for popular platforms and systems, in this case FishPig integrations for Adobe's Magento e-commerce platforms, can open the door to critical vulnerabilities and exploits.
[This blog is being actively updated as we learn more about the incident.]
The hackers injected malware into FishPig’s software, leading to the installation of the Rekoobe trojan on online e-commerce stores running FishPig’s plug-in software. This attack targeted FishPig's integrations for Magento, a very popular open source e-commerce platform for developing online marketplaces. However, plug-ins/integrations are used by a wide array of software platforms and systems, including SDLC systems and infrastructure such as Jenkins build servers.
Am I Impacted by hacked FishPig software?
The vendor has stated that it is best to assume that all paid FishPig Magento 2 modules have been infected.
How Did Attackers Compromise FishPig’s Software Supply Chain?
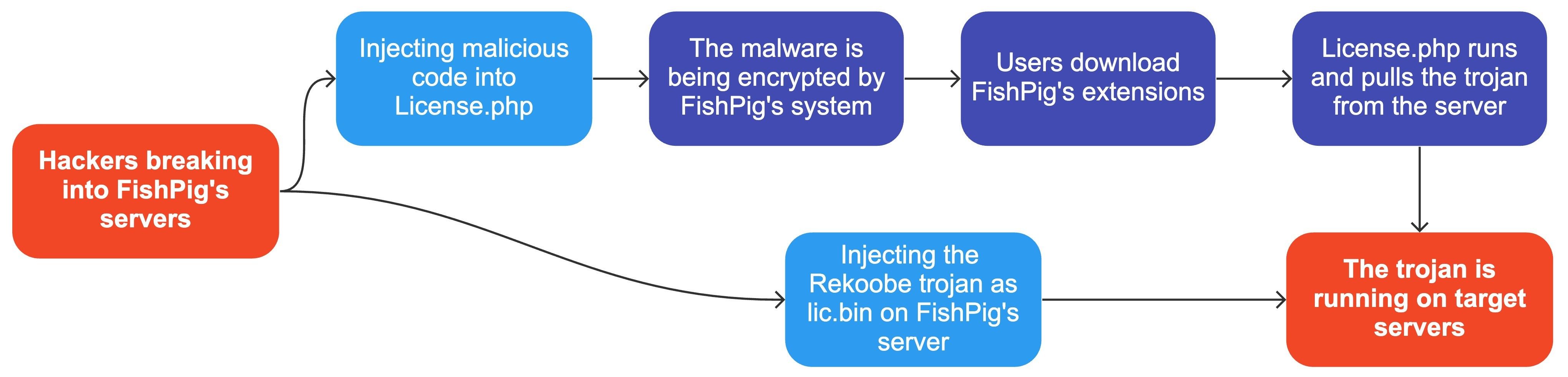
On August 6, 2022 or later, hackers managed to break into FishPig’s server in a way that is still unknown.
Hackers then injected malicious code into the Helper/License.php file, which is normally used to verify FishPig’s license on installed systems. Because FishPig’s system encrypts its software before it becomes available for download, this practically hides the malicious code from users and scanners.
Once the malicious code is deployed and runs on users' systems, the malicious code installs the Rekoobe remote-access trojan, which grants the hackers admin access to the servers.
What Do I need to Know About the Rekoobe Trojan?
During the attack, the hackers uploaded the Rekoobe trojan to FishPig’s servers, hiding it as a Linux library named lic.bin. Once running on the target servers, the malicious code was injected into License.php downloads lic.bin from the server.
Once launched, the Rekoobe trojan takes a few dangerous actions:
-
Loads its configuration.
-
Removes all malicious files from the disks.
-
Runs in the background, mimicking one of a set of standard system services.
-
Waits from commands from a C2 (command-and-control) server located in Latvia.
It is still not known if these backdoors have been exploited, but some speculate that the backdoors were meant to be sold to other hackers. Backdoor access in this context could be used maliciously to:
-
Forge websites to steal their users' credit cards.
-
Initiate ransomware attacks.
-
Steal code and assets.
-
Divert CPU and network resources.
-
Take advantage of the elevated privileges of infected servers to Infect further servers within their networks.
Detecting & Remediating the Rekoobe Trojan
FishPig has acknowledged the intrusion and its consequences. Refer to their status page for the latest remediation guidance.
To detect whether or not your website is infected, run the following script in the Magento root directory:
php <(curl -Ls https://fishpig.co.uk/rekoobe-sh)
As per FishPig’s statement, this tool checks all installed FishPig extensions for infection and provides advice on what to do next if your system is compromised.
Once detected, you should take the following steps to clean the malware from your server:
-
Remove all FishPig extensions installed on your site.
-
Restart your server to terminate malware running from memory.
-
Install the latest version of FishPig’s extension.
Best Practices to Reduce Software Supply Chain Risks Like These
As a software producer, you need to be resilient against these kinds of attacks on your software supply chain. You should take measures to properly manage your software supply chain resources and protect your SDLC assets to reduce your risk profile.
First, script files – such as the License.php file – should never be just hanging out on a server. You should manage your code in an SCM (source code management system), and protect your SCM from being tampered with by:
-
Controlling the access to the repositories.
-
Limiting who can push changes to your business critical repositories.
-
Enforcing branch-protection and multi-person reviews to your main branches.
-
Requiring MFA (multi-factor authentication) to your SCM accounts.
-
Monitoring your SCM to detect suspicious actions.
You should also control and secure the pipeline from source to production releases:
-
Use strict versioning rules to make sure that only well-produced code reaches your CI/CD pipeline.
-
Limit access to download sites and production registries to your CD systems.
-
Verify digests when fetching static assets that should not change regularly.
-
Adopt and require security practices including verifiable provenance documents to make sure that you only consume trusted software.
Legit Security provides protection from malicious 3rd party plug-ins/integrations for popular SDLC systems like Jenkins build servers and much more. Schedule a product demo or check out the Legit Security Platform to learn more.
Download our new whitepaper.


