We’re pleased to announce the launch of Legitify – an open-source security tool for GitHub users to automatically discover and remediate insecure GitHub configurations, at scale.
The risks behind GitHub misconfigurations
GitHub can be considered the “operating system” of many organization's development operation, and a single misuse can lead to critical incidents, data breaches and software supply chain attacks. It’s not about a lack of security features. GitHub can be configured to be fairly robust against a wide range of attacks. It has a wide range of security features and settings that enhance the safety of its users and organizations. Instead, it comes down to ensuring users know how to use these powerful capabilities to beef up their security.
However, it’s difficult and time-consuming to consistently enforce security across large GitHub implementations, and GitHub misconfigurations are a very common source of vulnerabilities. Manually enforcing consistency across large GitHub organizations is very labor intensive and prone to human error.
However, software supply chain attacks are on the rise and cause significant damage, as we’ve seen in many recent incidents. Generally speaking, SDLC misconfiguration risks are widespread and can lead to many dangerous exploits: denial of service attacks, maliciously changing your code, manipulating your CI/CD scripts, hijacking your production artifacts, stealing your secrets, and lateral movement into other critical assets.
Legitify your GitHub
Legitify is an open-source GitHub configuration scanner, built as a CLI tool, that helps Security, Dev or DevOps engineers manage and enforce their GitHub configurations in a secure and scalable way. It automatically detects security issues and provides remediation steps to address them. It was built with the following guidelines in mind:
-
Extensive Security Policies: We’ve created a library of security policies based on real-world experience and industry best practices. Each one contains detailed descriptions, severity, potential threats, remediation steps and any necessary metadata required to fix the issue.
-
Easy to Use: Legitify connects to GitHub via an access token and detects issues across various resource types: the organization itself, its members, its repositories and its actions (GitHub’s CI service) - and we plan to keep the list growing. Legitify provides the option to scan by specific GitHub organization/repository, a specific resource type, or to scan an entire GitHub organization across all resource types in one scan.
-
Fast: Legitify was designed and implemented with a lot of thought on performance and efficiency. The result is evident. Scan the security posture of your entire organization within a few seconds!
-
Enriched with OpenSSF Scorecard: Legitify is integrated with OSSF Scorecard so you can inspect your Scorecard values within Legitify to assess the security posture of your organization’s repositories using the Security Scorecard framework.
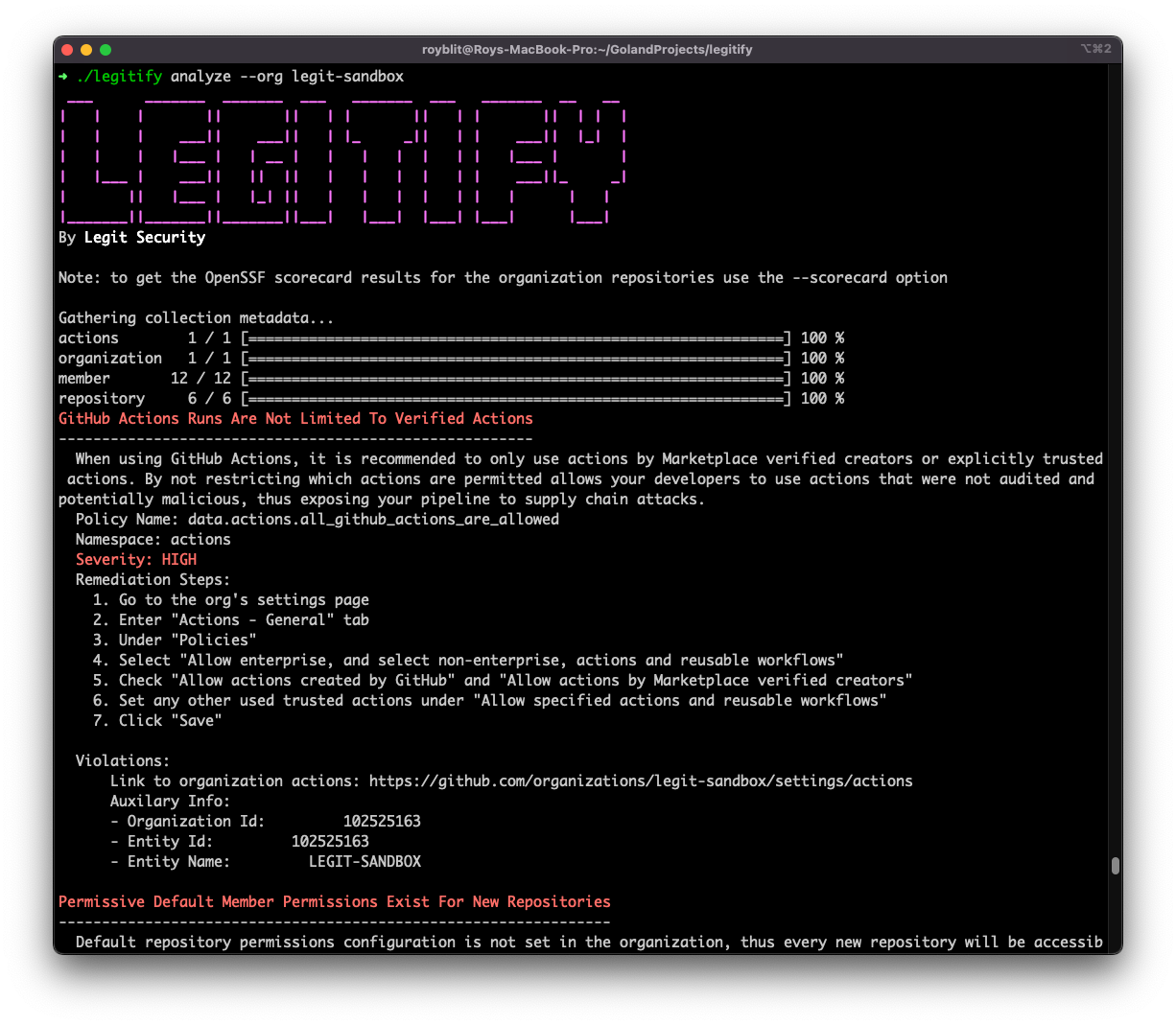

Examples of security risks that Legitify detects
Legitify identifies security risks related to misconfigurations of different GitHub resources. Here are just some examples:
-
Organization-level misconfiguration – 2-Factor Authentication Is Not Mandatory For The Organization
-
Repository-level misconfiguration – Default Branch Is Not Protected
-
Member-level misconfiguration – Stale Admin Detected
-
Actions-level misconfiguration – GitHub-Actions Runs Are Not Limited To Verified Actions
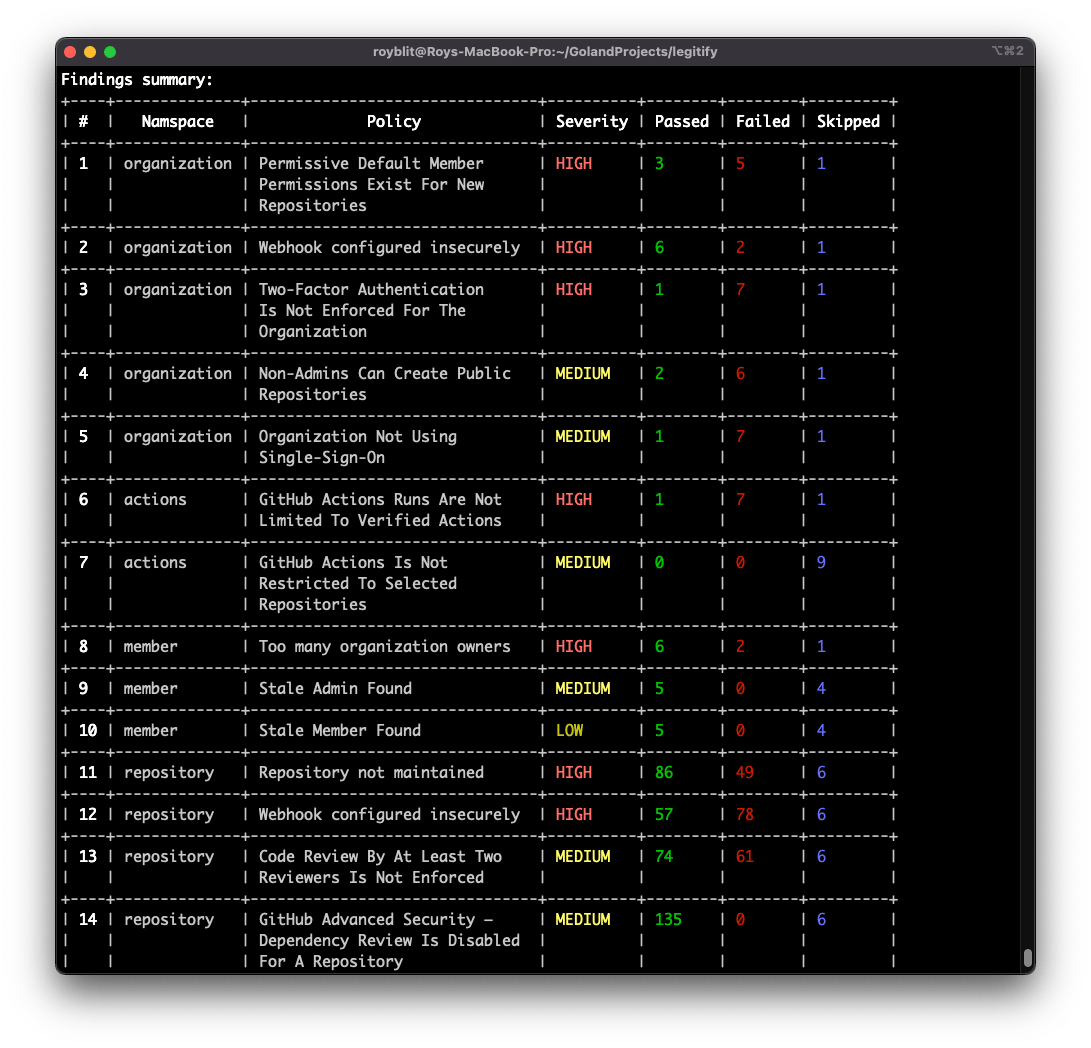
The full list is documented at legitify.dev. Each policy contains information about the security risk and actionable details on how to remediate the issue.
Moreover, Legitify can be run on a set of user-custom made policies, written in OPA, which is very flexible and easy to modify.
Where Legitify is going?
This launch is only the beginning of Legitify’s journey. Here at Legit Security we plan on investing resources to both maintain and expand Legitify’s capabilities. Here are a few of the features planned as part of the roadmap:
-
Expand the policies and cover more SDLC resource types
-
Automatic remediation
-
Enrich policies with more threat information
-
Automate and provision secure assets - for example - create a new secure repository
-
And much more…
Contributions Are welcome!
We encourage and appreciate any kind of contribution to Legitify. You can provide relevant information in the tool’s GitHub project. Legitify’s maintainers are devoted to the project and are happy to receive issues from users and pull requests from contributors. All issues / PR contributions will be addressed as soon as possible.
Download Legitify now and send us your feedback, we’d love to hear your thoughts and comments!
Download our new whitepaper.


