Continuous Compliance
and SBOM
Give your customers peace of mind in knowing that their application security posture is legit - and be able to prove it.
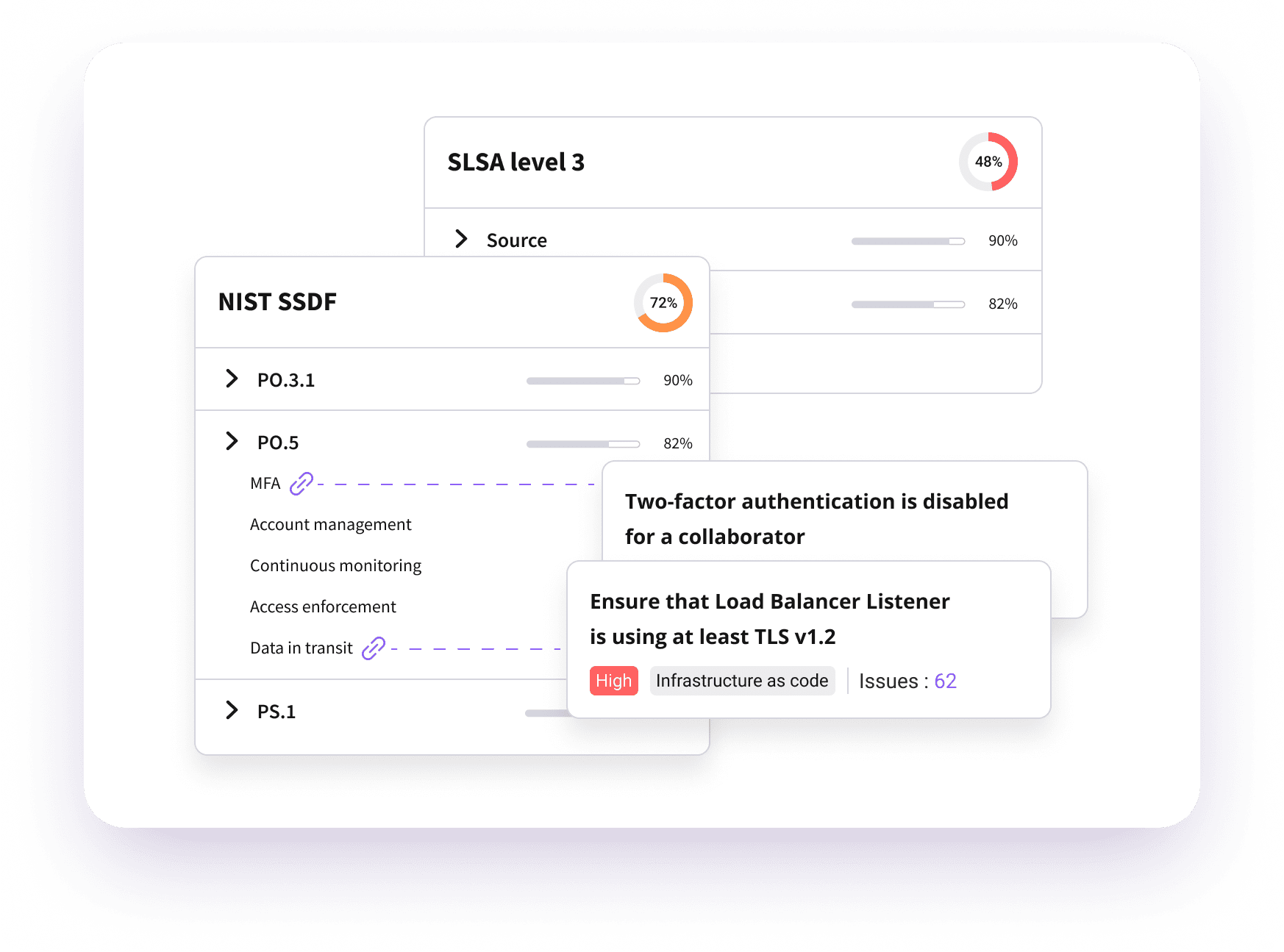
Align Security Controls To Regulatory Compliance
- Map security guardrails to specific regulations
- Support for ISO27001, SSDF, FedRamp, SLSA, NIST, SOC2, PCI DSS, CISA Attestation and more
- Identify security gaps to obtain compliance
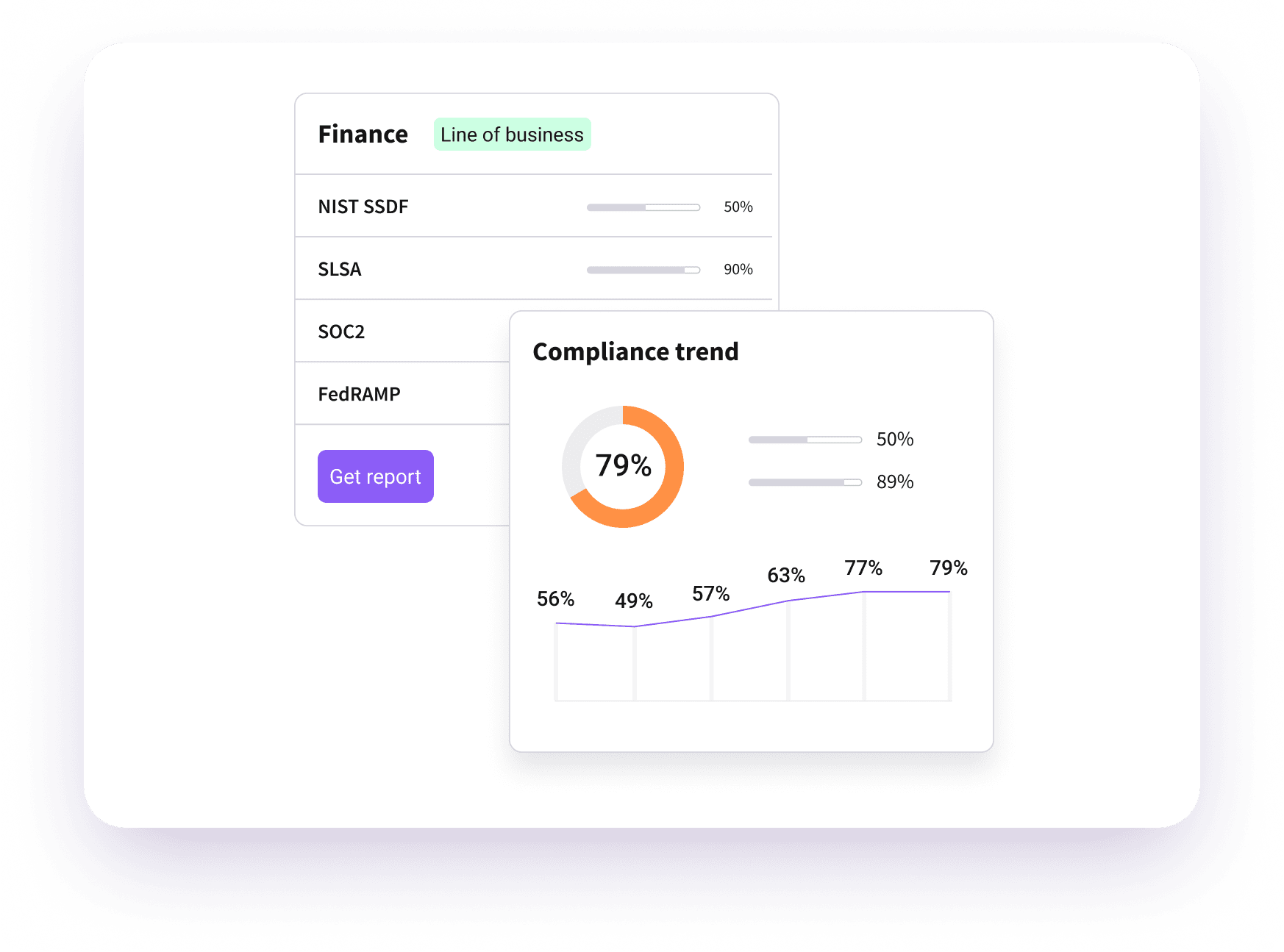
Continuous Assurance And Regulatory Drift Detection
- Real-time monitoring and alert on compliance violations
- Automated reporting for security posture compliance
- Ensure the security and integrity of each software release
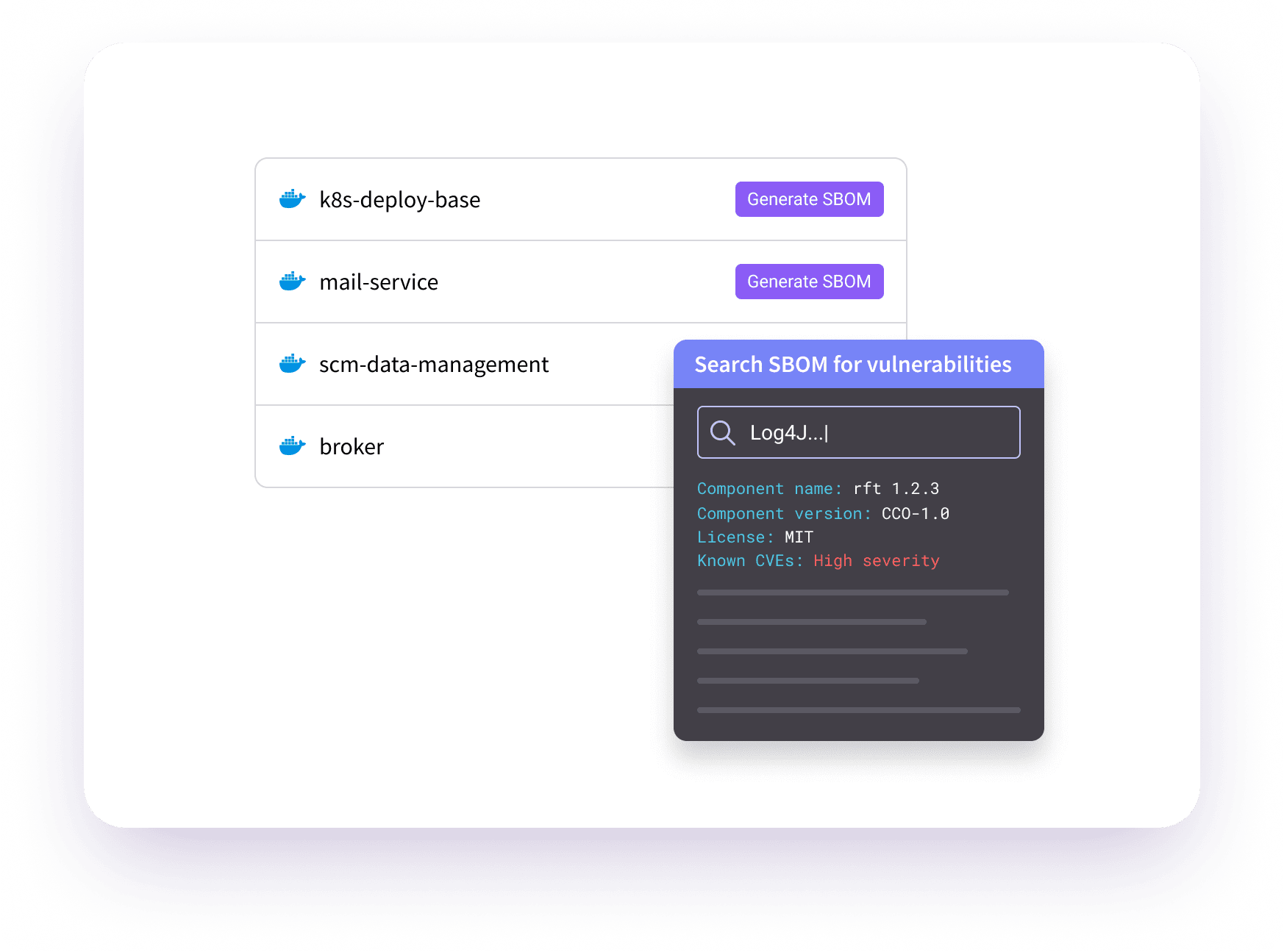
SBOMs And Software Attestations
- Create SBOMs and signed software attestations
- SBOMs support for all regulated formats
Related Resources
-
 Read Nowwhite papers
Read Nowwhite papersWhat You Need to Know About the Software Supply Chain Regulatory Landscape and SBOMs
This guide helps you understand the regulations around software supply chains.
-
.png?width=1400&height=800&name=Blog%20From%20Theory%20to%20Practice%20Navigating%20NISTs%20CICD%20Security%20Strategies%20(1).png) Read Nowblogs
Read NowblogsFrom Theory to Practice: Navigating NIST's CI/CD Security Strategies
As part of our mission for secure application delivery and to protect your software supply chain, we at Legit Security have been closely following the SSDF and all its related publications.
-
 Read Nowwhite papers
Read Nowwhite papersMore Coding, Less Remediating
How ASPM Boosts Developer Productivity and the Bottom Line
Request a Demo
Request a demo including the option to analyze your own software supply chain.
Request a Demo