CISA SSDF Attestation
CISA Attestation allows organizations to verify that they adhere to the NIST Secure Software Development Framework (SSDF) guidelines and comply with the controls described. Legit’s ensures you can validate your security program aligns with the four key areas of CISA Attestation.

Executive Sign-Off on Software Security
Software security supply chain attacks have created a newfound sense of urgency in validating the efficacy of software security programs. To that end, the U.S. government enacted requirements that companies selling software to the government validate they meet the SSDF framework requirements. Senior executive sign-off – CEO or COO – is required as part of CISA Attestation.
CISA Focus: Secure Development Environment
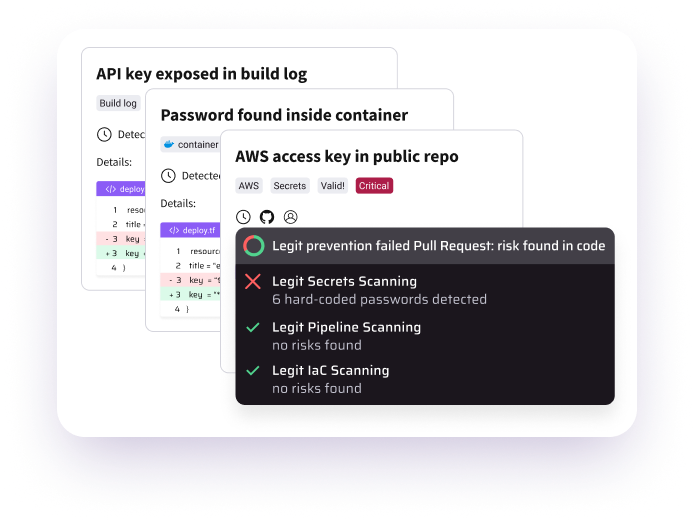
- Secrets Detection: Legit leverages AI and LLMs to discover and protect secrets across your entire SDLC.
- Developer Identification & Permissions: Legit instantly shows collaborators, as well as permissions.
- SDLC Visibility: Legit automatically and continuously discovers and maps all your developer tools and systems.
CISA Focus: Secure Software Supply Chain
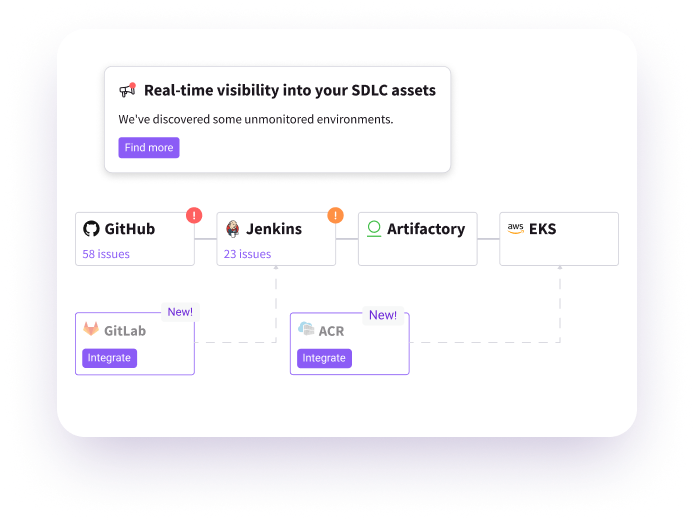
- SDLC Hardening: Legit offers the most comprehensive policies and best practices for protecting all assets in a software factory.
- SDLC Graph: Legit identifies how code progress through your pipelines for complete traceability in all your products.
- Code to Cloud: Legit Instantly traces any issue found in production back to the code for easy and fast remediation.
CISA Focus: Maintain Code and Artifact Provenance
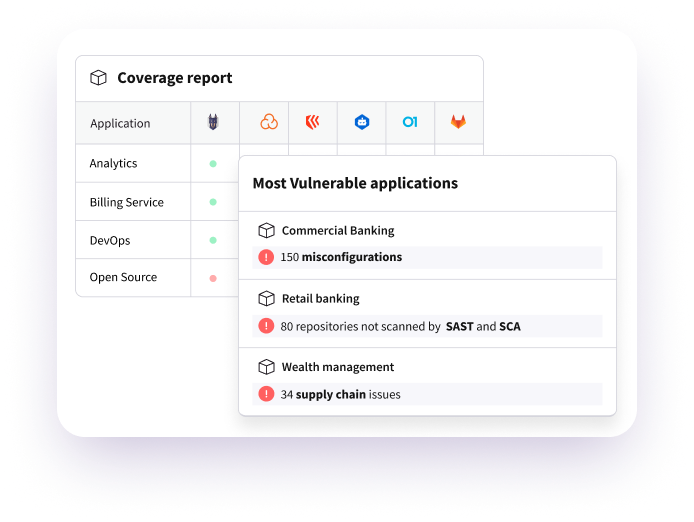
- Artifact Provenance: Legit delivers provenance records to verify and prove integrity of artifacts during the build process.
- Complete Inventory: Legit tracks all resources used in development, build and production, including repos, container images, Kubernetes resources and more.
CISA Focus: Check for Vulnerabilities
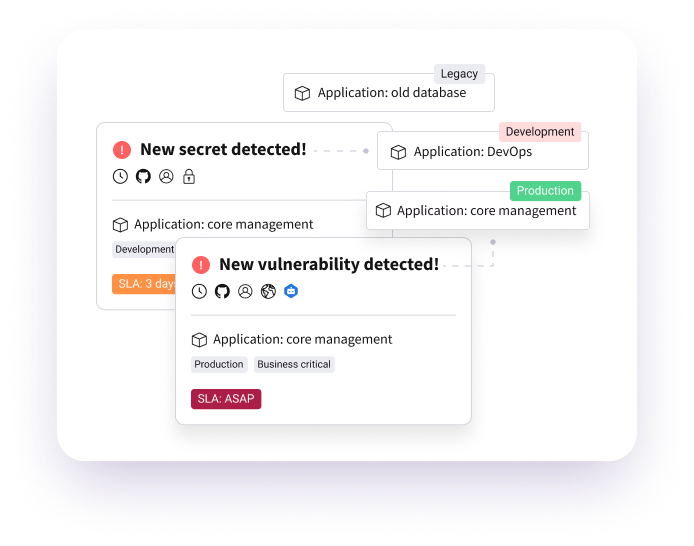
- Single Source of Truth: Legit integrates existing security scan tooling to aggregate, prioritize and remediate all issues from a single platform.
- Control Mapping: Legit provides complete visibility into where you have proper controls in place, as well as gaps, to support broader use of your existing tools.
- Extended Risk Visibility: Legit extends vulnerability, misconfiguration, and risk identification into areas of the SDLC largely ignored by existing application security tools.
Related Resources
-
 Read Nowinfographics
Read NowinfographicsOvercoming the Compliance Challenges of AppSec Infographic
Understand AppSec compliance challenges and how to address them.
-
 Read Nowblogs
Read NowblogsHow to Address CISA Attestation
Get details on the CISA Attestation, how to address it, and how Legit can help.
-
 Read Nowdatasheets
Read NowdatasheetsAddressing CISA Attestation
Learn more about CISA attestation and how Legit policies map to its requirements.
See more
Related Posts
ASPM Knowledge
Request a Demo
Request a demo including the option to analyze your own software supply chain.