Supply chain attacks
Secrets create an attacker entry point to conduct a more significant supply chain attack.
Legit is an AI-native ASPM platform that automates AppSec issue discovery, prioritization, and remediation. A trusted ASPM vendor for your AppSec and software supply chain security programs.
AI is revolutionizing development - making it faster, smarter, and more autonomous. It’s also rewriting the rules of application security. Traditional AppSec tools weren’t designed for AI-driven dev processes. Legit is here to help.
Secrets are vital to software development today; modern apps use hundreds of secrets to operate. API keys, access tokens, credentials, and other secrets ensure the security of applications and data, and enable non-human identities to communicate. And, secrets are everywhere, found far beyond source code. With such value comes risk – secrets are a prime target for attackers seeking to infiltrate your software supply chain.
Secrets are everywhere – far beyond source code
Secrets are continually added by developers
Secrets live in history and shadow assets forever
Secrets scanning is burdened with false positives
Secrets create an attacker entry point to conduct a more significant supply chain attack.
Developers spend significant time tracking down and removing secrets.
Addressing a secret already deployed doesn’t end in simply revoking it.
Make sure your software development organization is aware
of the different locations where sensitive data can get exposed.
Employ automated secrets scanning that covers all assets where secrets can hide, including source code, build logs, artifacts, documentation pages, etc.
With checks on endpoints, before merge, and scans of codebase.
Ensure no misconfigurations are increasing risk.
Legit uncovers secrets wherever they reside in your developer environment because source code is only the tip of the iceberg. From ticketing & ITSM systems, artifact registries and shared workspaces such as Confluence, Jira, and Slack, to your developers’ personal GitHub accounts, we go deep to identify every secret. We even unearth secrets hiding in Git history.
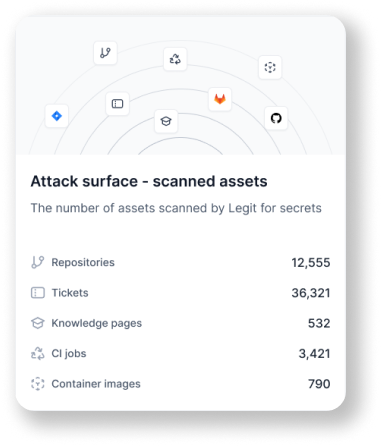
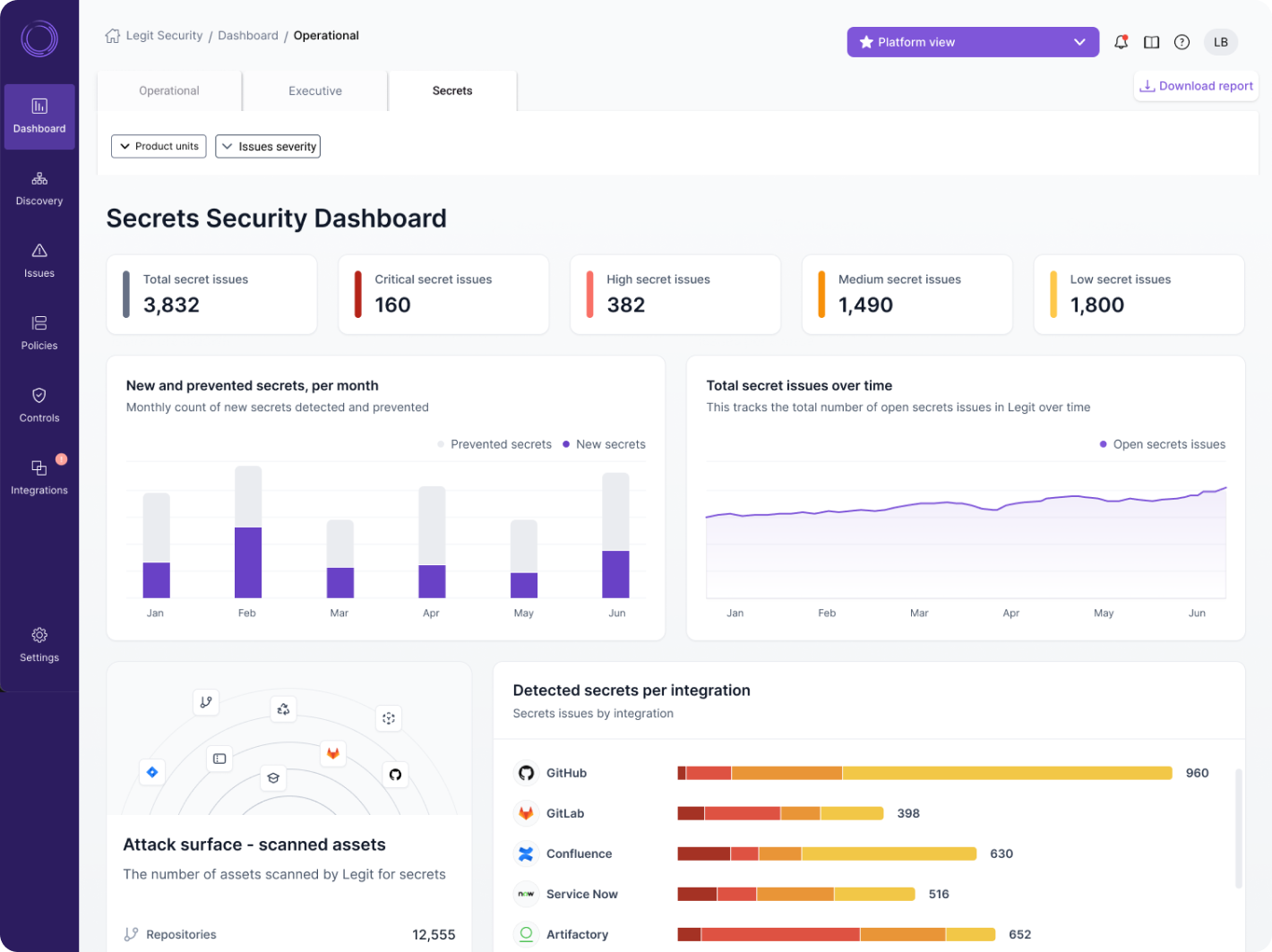
Legit analytics provide a deep view of secrets and the associated security activities. With our centralized dashboard, you have one view of all secrets detection and prevention across the enterprise. Your teams will benefit from a simple, clear way to gain a complete view of your secrets posture.
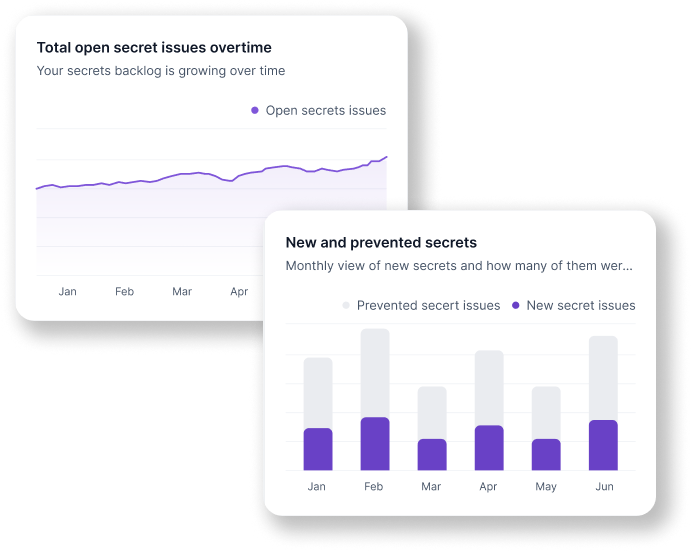
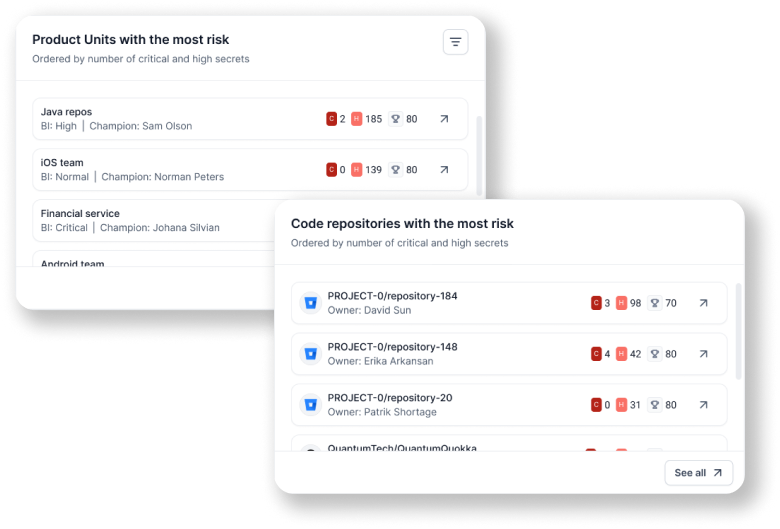
Legit helps you to prioritize developers’ work based on risk to the business. We dive deep into your secrets to prioritize remediation based on factors such as severity, source, repo, and user. Legit’s automation and orchestration capabilities enable you to immediately fix any existing secrets. Legit also provides a simple view of new secrets, plus remediation and backlog trends so you can assess the effectiveness of your AppSec program.
.png?width=521&height=395&name=Remediation%20(2).png)
Legit allows you to stop the bleeding with automated guardrails that can actively prevent new secrets from entering the developer environment. This can be extended all the way to the individual developer endpoint with the Legit CLI.
.png?width=521&height=395&name=Prevention%20(2).png)
Unlike open-source tools, Legit has a continually learning engine with a low rate of missed detections to find all secrets in your SDLC, while the platform delivers extensive context and prioritization capabilities to limit the impact of false positives.
CISOs
Secrets are a top area of risk to the business. Legit provides an executive-level view of your secrets posture so you can understand and communicate risk status and trends.
AppSec
Exposed secrets open up avenues to infiltrate your applications and software supply chain. Legit helps you identify and fix the issues that matter most.
Cloud Engineering
Secrets are the key to allowing cloud services to interact, communicate, and do their jobs. With Legit, you can protect these lifelines and ensure your services are secure and resilient.
Platform Engineering
Developers rely on secrets to build and deliver the apps your business relies on. With Legit, you can ensure the platform services that enable developers to do their job remain secure and protected.
Security Operations
Because secrets are so prevalent, they play a central role in expanding your overall attack surface. With Legit, you can reduce this risk by ensuring secrets are identified, remediated, and prevented.
A developer can choose to temporarily hard-code a secret, and when merging the final revision to the main branch, remove the secret and switch to a more secure option. Unfortunately, people make mistakes, and many times those secrets are forgotten in the code.
Secrets are often shared through these services, such as Confluence, SharePoint, etc., without realizing the potential damage.
Build logs often contain sensitive secrets, which can end up exposed if they are configured to be publicly accessible.
When creating a final application artifact, sensitive data can be packed by mistake.
Experience first-hand the power of the preventative capabilities Legit enables with a 2-week free trial.
Start Your Free Trial
Get an overview of Legit's secrets scanning capabilities.

Find out how secrets end up in your code and how to protect them.

Find out the top unknown SDLC risks we unearth, plus how to prevent them.
Request a demo including the option to analyze your own software supply chain.
Request a Demo