Legit Security in the News
Let Legit Security help you manage your privacy program so you don’t have to worry about the risks of noncompliance. In five minutes, your website will go from liability to a shining example of how to do privacy right.
Sign up for our newsletter
Latest Press Releases








Get more from our blog
Legit Security secures your software supply chain environment with risk scoring.
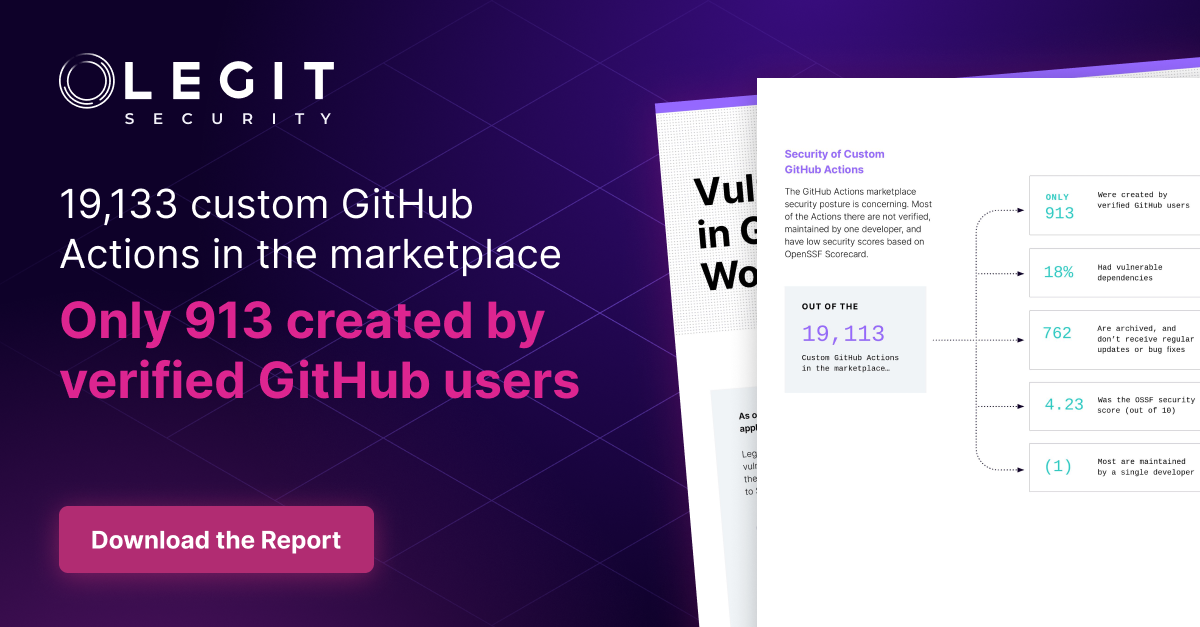
Security of Custom GitHub Actions
Legit Security | Security of Custom GitHub Actions. Get details on Legit's research on the security of custom GitHub Actions.
Read More
Announcing The State of GitHub Actions Security Report
Legit Security | Announcing the State of GitHub Actions Security Report. Get details on Legit's research on the security of GitHub Actions.
Read More
What You Need to Know About the EU Cyber Resilience Act
Legit Security | What You Need To Know About the EU Cyber Resilience Act. Understand what the CRA entails and how to comply.
Read MoreSchedule A Demo
Book a 30 minute demo including the option to analyze your own software supply chain, if desired.