What are different solution approaches to software supply chain security and what are the Pros and Cons for your organization? What is the modern definition of software supply chain security and why is it so important, now more than ever, to increase your focus on this aspect of cybersecurity? This blog will answer those questions and provide guidance to help support your decision to implement a solution.
What Is a “Software Supply Chain”?
A software supply chain is the ecosystem of systems, infrastructure, code, people, and processes involved in developing and releasing software. We define the software supply chain as the pre-production development environment from Source Code Management to Build to Artifact Repo, right up until production deployment. A compromise within a company’s software supply chain can disrupt business operations, incur regulatory penalties and fines, negatively impact downstream customers, and incur brand and repetitional damage.
Your software supply chain consists of everything that’s used to develop, build, and publish software, including:
- Source code
- 3rd party components and plug-ins
- Software libraries
- Systems, tools, and infrastructure
- Pipelines and processes
- Dependencies
One simple way to visualize the software supply chain is with the SLSA framework and diagram (see below). SLSA has become a standard for understanding what the software supply chain is and provides enterprises with a framework, checklist, and standards to prevent tampering and improve the integrity of organizational software development.
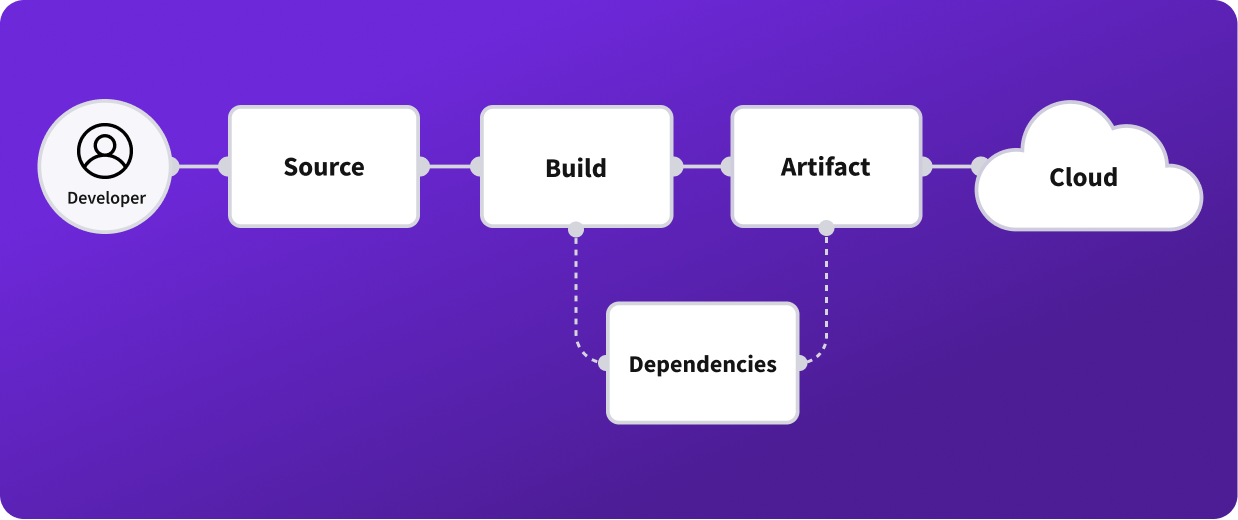
What is a software supply chain diagram
It is worth noting that SBOMs, or Software Bill of Materials, are rapidly becoming an important aspect of software supply chain governance and security. SBOMs provide a detailed list of all of the ingredients within your application's code. Maintaining an SBOM helps with application management and regulatory compliance and helps defend against vulnerabilities by rapidly identifying if a component within your application is at risk.
An SBOM does not assure that your application or software supply chain is secure, but it is an important step in the right direction. Although there is not a single definitive standard for SBOM, the National Telecommunications and Information Administration or NTIA has defined the minimal requirements.
Why Now’s the Time to Focus on Securing Your Software Supply Chain
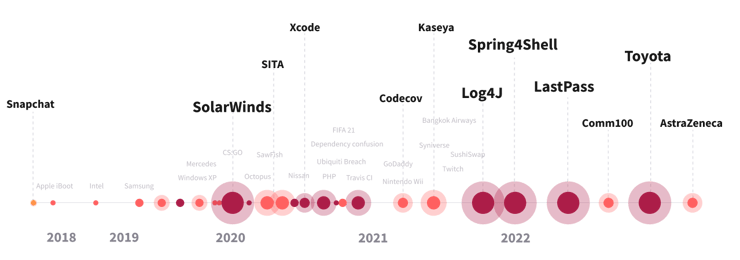
There’s never been a better time than now to boost your software supply chain security. The pre-production software development environment has become increasingly diverse, complex, and susceptible to attack. It can be extremely difficult to manually track changes, updates, and vulnerabilities across this environment, which makes it easier for malicious attackers to exploit openings and weaknesses. Unfortunately, breaches have become more frequent than ever, which is why it’s important to focus on securing your software supply chain now.
Some of the most notable breaches that have disrupted the entire software supply chain industry include:
- SolarWinds
- This attack was a key catalyst for the development of the software supply chain security category. A system management tool for network and infrastructure monitoring was hacked globally as a zero-day vulnerability, where the Sunburst malware allowed threat actors to gain access to several government systems and thousands of private systems around the world.
- Codecov
- The attack was performed by very sophisticated attackers who exploited a mistake in how Codecov built docker images. They used this to modify a script allowing them to send environment variables from Codecov customers to a remote server.
- Kaseya
- Kaseya VSA is a product commonly used by MSPs to manage their clients' IT environments. It was used as part of a supply chain attack delivering REvil ransomware to thousands of organizations.
- Log4J
- Apache Log4J’s Log4Shell is a well-known zero-day vulnerability highly susceptible to attack. Attacks on institutions via Log4J dependencies have emerged in large numbers.
While the timeline of all of the most notable events and CVEs can be mapped, we obviously don't know what major event is just around the corner. That said, certain patterns are being followed and you can read about the three riskiest attack patterns for the software supply chain to learn more.
Protection Against An Exploding Attack Vector – Legit Security Homepage
The best way to avoid attacks and not repeat mistakes is to evolve your cybersecurity programs. Having a security-forward mindset in an organization from the top down helps ensure that you can respond and adapt quickly to major, industry-impacting events such as the four above, no matter what or when they occur. DevSecOps is a great example of a security-forward program or initiative specific to DevOps that is sure to become more prominent as these types of attacks continue.
No matter if talking about DevSecOps or a more traditional Application Security initiative, the push continues for the use of security automation and tools that not only catch risk and vulnerabilities but also make the security teams that use them more effective and efficient. Within the context of software supply chain security, which products and tools are the right fit for your organization?
Different Types Of Software Supply Chain Security Solution Approaches
When it comes to software supply chain security, there are new solutions available in the market. Some of these solutions include software composition analysis, vulnerability management, automated testing, and secure coding practices. Software composition analysis helps in identifying and mitigating open source vulnerabilities, while vulnerability management monitors and detects vulnerabilities throughout the software lifecycle. Automated testing helps in identifying security flaws at an early stage, and secure coding practices involve using guidelines to ensure code is developed with security in mind. These types of solutions may differ in their approach, but they all aim to enhance software supply chain security and reduce the risk of cyber attacks.
While we could deep dive into the various solutions, our focus here is on the approach, and each has its own unique traits and characteristics. It can be difficult to determine which solution approach is the best fit for your organization, they share some commonalities between them. Software supply chain risk management is made easier when you have broad visibility into your attack surface and can surface vulnerabilities before attacks occur. Ultimately, each security solution approach has its pros and cons, and only you will know which is best for your unique needs.
Provide Visibility And Analysis Of The Entire Software Supply Chain
Visibility into SDLC systems and infrastructure is foundational to understanding the entire software supply chain and securing development pipelines. Within the SDLC, there is a vast array of components, systems, repositories, and tools used.
Having instant insight into all these related components (i.e., the software supply chain) allows organizations to uncover related security issues. You can’t protect assets you don’t even know are there. A solutions approach prioritizing visibility enables organizations to analyze risk and prioritize where to focus remediation efforts.
Pros
- Comprehensive, visual inventory that's continually updated
- Reveal unknown, misconfigured, and vulnerable SDLC systems and infrastructure
- See which pipelines are secure, and which are vulnerable
- Centralized visibility over the location, coverage, and configuration of your existing security tools and scanners
- Ability to identify developers and contributors effectively
- Ability to identify and manage connected components
Cons
- Technology is required to automate and scale this approach
- Security issues are identified with greater context, but they still must be remediated.
Score And Prioritize Software Supply Chain Security Risks
Issues, issues, issues. Security teams everywhere are outnumbered by security issues and – without the proper tools and frameworks – struggle to prioritize which issues should be prioritized over others. One approach to prioritization is creating a risk score based on an agreed-upon rubric. By doing this, CISOs and their security teams can better manage risk and report trends to stakeholders.
Another approach is to focus on the relative security score of a development team or product line. Software supply chain security spans both application security and development teams, which can create friction for security teams pleading with their development teams to develop their applications securely. A scoring system that helps compare the relative security posture between different development teams can expedite the cooperation of less secure development teams in need of improvement when they learn they are scoring worse than another development team.
Pros
- Helps teams focus on the most important issues
- Gamifies security for development teams
- Aids reporting of risk trends in an actionable way
- Scores can be continuously updated with proper tooling
Cons
- Must align and agree on a scoring system
- Requires education on what attributes make up the score
Robust Features for governance and regulatory compliance
A compliance-oriented approach to software supply chain security can help provide assurance to organizations that they are compliant with regulatory and internal security mandates. Manually mapping security policies to compliance frameworks can be resource-intensive and, in some cases, nearly impossible. Software supply chain security tools can help automate this task. Further, they can include robust reporting features and drift alerts that align with compliance frameworks, such as SOC2, OpenSSF, NIST, and ISO27001.
Keeping track of your compliance status in real-time helps avoid surprises during compliance audits and provides important business context to security issues. If security issues are automatically tagged with the compliance framework they are related to, it’s easier to identify and prioritize those issues for remediation.
Pros
- Avoid fines or penalties for falling out of compliance
- More easily provide evidence to auditors of security practices
- Helps organizations govern compliance at scale
- Ensure industry-based requirements are met
- Keep up with the evolving compliance requirements in software supply chain security
Cons
- Regulatory mandates often lag security best practices. Compliance with regulations is not a substitute for following modern best practices.
It's worth noting that different approaches have features to support cybersecurity governance. Governance encompasses accountability frameworks, decision-making hierarchies, defined business objective risks, mitigation playbooks, and oversight processes and procedures. Different solutions are better equipped to support organizations. How effective these solution features integrate with operations to help prevent interruption from cyber-attacks is key.
Let the Experts Help Boost Your Software Supply Chain Security
A software supply chain is the ecosystem of infrastructure, systems, processes, and people involved in developing software. Legit Security defines the software supply chain as the pre-production development environment from Source Code Management to Build to Artifact Repo, right up until production deployment.
With major security breaches like Log4J, SolarWinds, and Codecov and an expected 3x-6x increase in software supply chain attacks, securing your development infrastructure is more important now than ever.
There are different types of software supply chain security solution approaches and each has benefits and disadvantages. The Legit Security Platform strives to embed the best aspects each approach has to offer while minimizing the drawbacks. Legit Security provides you with the best visibility into your development pipelines while also providing you with scoring and prioritization mechanisms so that you can focus on the most critical risks. We include compliance contextualization along with security issues, which allows you to filter issues by compliance framework.
Legit secures your applications from code-to-cloud with automated SDLC discovery and analysis capabilities and a unified application security control plane that provides visibility, security, and governance over rapidly changing application development environments.
To learn more about Legit Security and preventing software supply chain attacks, book a demo today.